# An Open Ecosystem
Linux is an open-source community that focuses on sharing power and responsibility among people instead of centralizing within a select group. The Linux kernel – which acts as the foundation for many Linux-based distributions – is built on an even older framework that matured alongside computers.
The [PDP-7](https://en.m.wikipedia.org/wiki/PDP-7) ran the first Unix code – used for creating the demo video game [Space Travel](https://en.m.wikipedia.org/wiki/Space_Travel_(video_game)).
| [](https://hub.subspace.services/uploads/images/gallery/2025-05/1000000479.jpg) | [](https://hub.subspace.services/uploads/images/gallery/2025-05/1000000480.png) |
## An Accidental Movement
Unix was a general-purpose operating system that began to take shape in the mid-1960s. This was a collaborative project between the [Massachusetts Institute of Technology](https://en.m.wikipedia.org/wiki/Massachusetts_Institute_of_Technology "Massachusetts Institute of Technology"), [Bell Labs](https://en.m.wikipedia.org/wiki/Bell_Labs "Bell Labs"), and [General Electric](https://en.m.wikipedia.org/wiki/General_Electric "General Electric"). Academic researchers within the burgeoning computer science field experimented with the potential for [time-sharing](https://en.m.wikipedia.org/wiki/Time-sharing) to innovate what was possible with these new digital machines.
[](https://hub.subspace.services/uploads/images/gallery/2025-05/1000000452.png)
[Unix](https://en.m.wikipedia.org/wiki/Research_Unix) itself was based on an even older exploration in computers – an operating system called [Multics](https://en.m.wikipedia.org/wiki/Multics "Multics"). Pronounced as "[eunuchs](https://en.m.wikipedia.org/wiki/Eunuch "Eunuch")", the name itself was intended as a pun on it's predecessor. Multics had yielded truly innovative ideas, but it's exploratory nature wasn't immediately profitable and the project was eventually
shuttered.
[](https://hub.subspace.services/uploads/images/gallery/2025-05/1000000461.png)
> What we wanted to preserve was not just a good environment in which to do [programming](https://en.m.wikipedia.org/wiki/Computer_programming "Computer programming"), but a system around which a fellowship could form. We knew from experience that the essence of communal computing, as supplied by remote-access, [time-shared](https://en.m.wikipedia.org/wiki/Time-sharing "Time-sharing") machines, is not just to type programs into a [terminal](https://en.m.wikipedia.org/wiki/Computer_terminal "Computer terminal") instead of a [keypunch](https://en.m.wikipedia.org/wiki/Keypunch "Keypunch"), but to encourage close communication.
>
> — [Dennis Richie](https://en.m.wikipedia.org/wiki/Dennis_Ritchie), UNIX pioneer
The original [AT&T](https://en.m.wikipedia.org/wiki/AT%26T_Corporation "AT&T Corporation") Unix – created in 1969 – was a proprietary and closed-source operating system first investigated by [Bell Labs](https://en.m.wikipedia.org/wiki/Bell_Labs). As the result of a result of a 1958 ruling by the US Department of Justice, [AT&T was forbidden from entering into the computer business](https://historyofcomputercommunications.info/section/2.13/Antitrust,-Computer-Inquiry-II-and-the-Break-up-of-AT&T-1973-1984/) under consent decree. This was a part of the larger [breakup of the Bell systems](https://en.m.wikipedia.org/wiki/Breakup_of_the_Bell_System) that continued through the 1980s.
[](https://hub.subspace.services/uploads/images/gallery/2025-05/1000000462.jpg)
This meant that AT&T was required to license it's non-telephone technology to anyone that asked. While Unix was intended for use within their labs, they began licensing it to colleges and corporations for a modest fee. This lenient licensing scheme played an important part in the widespread adoption of Unix and the eventual open-source movement.
### Cathedral and the Bazaar
During the early days of computers, programmers and researchers were one and the same. While developing programming languages like [C](https://en.m.wikipedia.org/wiki/C_(programming_language)) – the backbone of Unix – we were also exploring what computers could accomplish for the first time. To that end, it was common to share software and learn from each other while studying computing.
[Cathedral and the Bazaar](https://en.m.wikipedia.org/wiki/The_Cathedral_and_the_Bazaar) was a foundational book by [Eric S. Raymond](https://en.m.wikipedia.org/wiki/Eric_S._Raymond "Eric S. Raymond") about opposing software project management styles.
Unix was revolutionary not only as an operating system, but because it came bundled with a complete copy of the source code used to build it. This allowed researchers to modify the code to fulfill their needs while also enabling corporations to create their own custom Unix distributions – for use in-house or as a marketable product. This led to a proliferation of Unix operating systems, each with exciting new features.
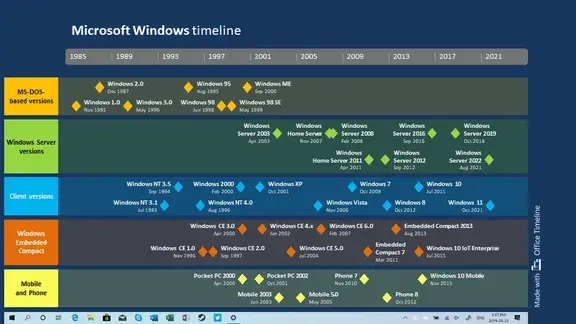
Windows vs Mac vs Linux vs Unix timeline graphic
[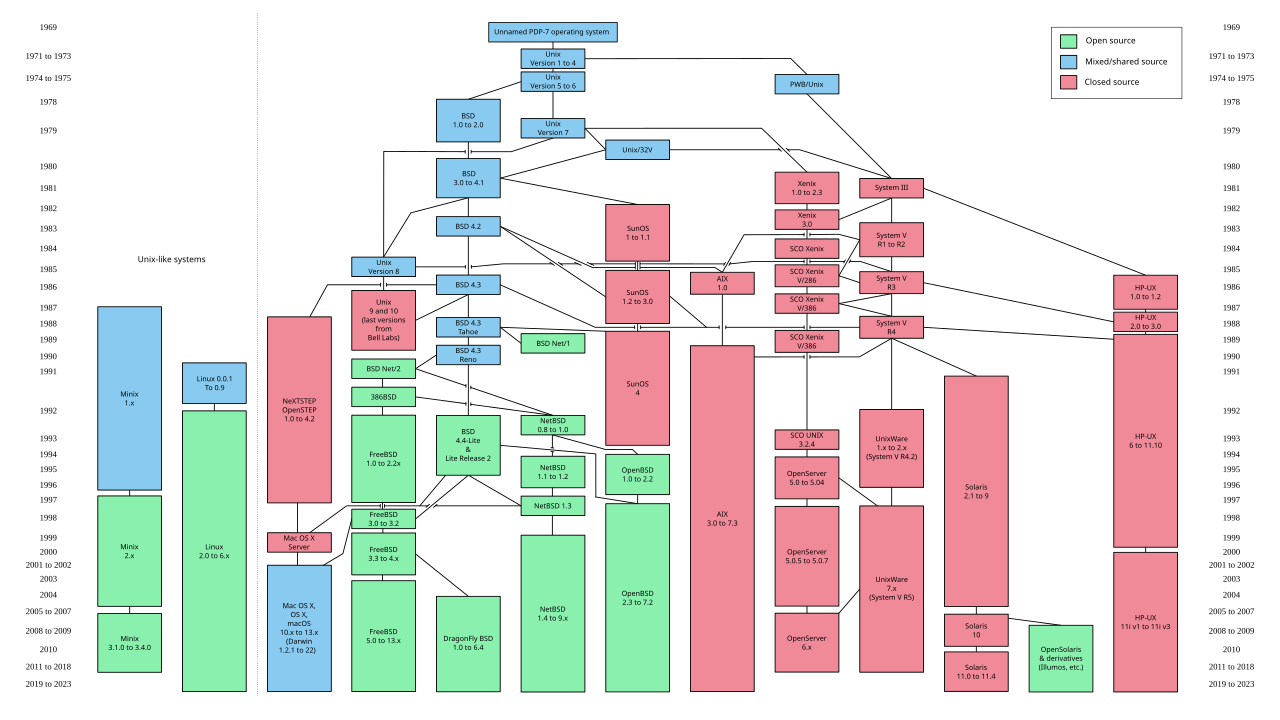](https://hub.subspace.services/uploads/images/gallery/2025-05/1000000439.png)
[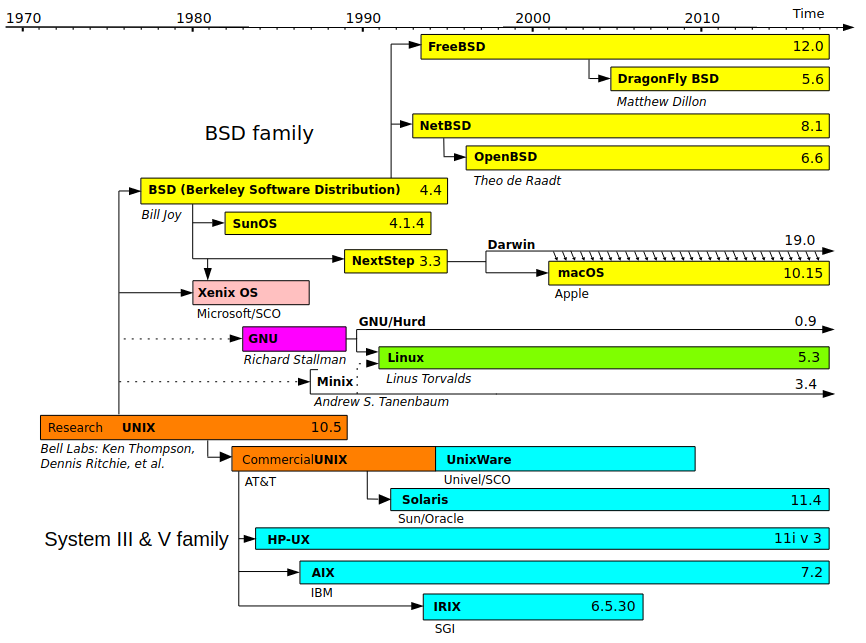](https://hub.subspace.services/uploads/images/gallery/2025-05/1000000440.png)
[](https://hub.subspace.services/uploads/images/gallery/2025-05/1000000443.webp)
Software – like hardware – became increasingly commercialized throughout the 1970s. Corporations sought to mold hardware into compact personal devices while simultaneously fashioning software into the [killer application](https://en.m.wikipedia.org/wiki/Killer_application) that would draw consumers to their products. The [Unix Wars](https://en.m.wikipedia.org/wiki/Unix_wars) throughout the 1980s exacerbated the friction between vendors as the operating system became fragmented between multiple competing standards.
As corporations navigated this space, many preferred to follow the proprietary development model. These release cycles are often measured in years – meaning that software was released as polished product with meticulous planning put into [final 'gold' release](https://en.m.wikipedia.org/wiki/Software_release_life_cycle#RTM). On the flip side, bug fixes and feature requests could take years to manifest in the publicly available product. Important software updates may never emerge – or may even be released as part of the product's successor.
This 'release late—release rarely' philosophy arises when the software developers [regard their project as a consumer product.](https://dsbscience.com/freepubs/linuxoverwindows/node3.html) While the product is marketed towards consumers, their role in the creative process is rather limited. Their feedback is often collected reactively during formative beta testing – or even after the product is released to the public.
[Proprietary software](https://en.m.wikipedia.org/wiki/Proprietary_software) is often "closed-source", meaning that the code to create it is private and legally protected – or even a [trade secret](https://en.m.wikipedia.org/wiki/Trade_secret). The code is compiled into a [binary file](https://en.m.wikipedia.org/wiki/Binary_file) containing the raw binary data – ones and zeros – used to control a computer system. This data it is not human-readable and only works on a specific platform – such as Windows, MacOS or Debian Linux.
This makes it relatively difficult to [reverse engineer](https://en.m.wikipedia.org/wiki/Reverse_engineering), but it also means that the code wasn't compiled to run efficiently on your specific computer system. Instead, it is compiled to meet 'minimum system requirements' and more advanced hardware is rarely leveraged to your advantage.
### Software Freedoms
During the 1970s, the original computer [hacker culture](https://en.m.wikipedia.org/wiki/Hacker_culture) – who enjoyed the creative challenge of overcoming hardware and software limitations – formed within academic institutions.
It was around this time that the [Free Software Movement](https://en.m.wikipedia.org/wiki/Free_software_movement) began to take shape. Researchers continued to develop software collaboratively by sharing their discoveries and the source code that powered them. This was foundational to the continued growth of the [Unix experiment](https://en.m.wikipedia.org/wiki/Research_Unix).
[](https://hub.subspace.services/uploads/images/gallery/2025-05/1000000506.jpg)
In 1984, [Richard Stallman](https://en.m.wikipedia.org/wiki/Richard_Stallman) resigned from his position at MIT citing that proprietary software stifled collaboration by limiting his labs ability to share source code. He began work on the GNU Project – which stands for *GNU's Not Unix* – and represented an idealized ,"free" operating system. It behaved almost exactly like Unix to attract developers, but the source code would be available for anyone to modify.
[](https://hub.subspace.services/uploads/images/gallery/2025-05/1000000463.png)
> The word "free" in our name does not refer to price; it refers to freedom. First, the freedom to copy a program and redistribute it to your neighbors, so that they can use it as well as you. Second, the freedom to change a program, so that you can control it instead of it controlling you; for this, the source code must be made available to you.
>
> — [GNU's Bulletin, Volume 1](https://www.gnu.org/bulletins/bull1.txt)
The [Free Software Foundation](https://en.m.wikipedia.org/wiki/Free_Software_Foundation) he sparked – through his call-to-action known as the [GNU Manifesto](https://en.m.wikipedia.org/wiki/GNU_Manifesto) – initially caused some confusion. He often had to explain that he meant "free" as in "freedom" not as in "beer". This led to the foundation of the movement: [the four software freedoms](https://en.m.wikipedia.org/wiki/The_Free_Software_Definition).
| Counter\_1
| **Freedom 1**
The freedom to run the program as you wish, for any purpose.
|
| Counter\_2 | **Freedom 2**
The freedom to study how the program works, and change it so it does your computing as you wish.
|
| Counter\_3 | **Freedom 3**
The freedom to redistribute copies so you can help your neighbor.
|
| Counter\_4 | **Freedom 4**
The freedom to distribute copies of your modified versions to others. By doing this you can give the whole community a chance to benefit from your changes.
|
Fulfilling these freedoms required unrestricted access to the underlying source code. Through GNU, a new [decentralized model of development](https://ieeexplore.ieee.org/document/9233046) emerged that enabled everyone to contribute bug fixes, code suggestions and feature requests. Communication took place primarily on internet [newsgroups](https://en.m.wikipedia.org/wiki/Newsgroup) like [Usenet](https://en.m.wikipedia.org/wiki/Usenet) – one of the first examples of a public-facing [digital bulletin board](https://en.m.wikipedia.org/wiki/Bulletin_board_system).
[](https://hub.subspace.services/uploads/images/gallery/2025-06/1000000508.png)
GNU developed in sharp contrast to proprietary software with many open-source projects following the 'release early—release often' development philosophy. These software programs are not generally viewed as a consumer product, but as a tool to reach an end.
While these projects may feel less polished, users have the power to add their voice throughout the entire development process. This means the potential for bugs to be fixed promptly and – depending on community feedback – features can be quickly integrated into the ongoing evolution.
The [GNU Project](https://en.m.wikipedia.org/wiki/GNU_Project) is an umbrella for the hundreds of smaller projects that are necessary to build an operating system from the ground up. While developed through collaboration, these constituent projects are produced independently of the others.
## Modular by Design
While lying the foundations for Unix, computer scientists were careful to consider it's [design philosophy](https://en.m.wikipedia.org/wiki/Unix_philosophy). They decided that Unix should provide a simple set of tools – each able to perform a [limited function with well-defined parameters](http://www.catb.org/~esr/writings/taoup/html/). This facilitated a [modular](https://en.m.wikipedia.org/wiki/Modular_design) and decentralized approach to developing the new operating system.
This philosophy disconnected the lifecycle of applications from each other – as well as from the operating system. This led to a [rolling release model](https://en.m.wikipedia.org/wiki/Rolling_release) where individual software packages were updated frequently and released quickly. These modular programs could be maintained independently and development teams only needed to coordinate how their modules would communicate – such as a mutually-defined [API](https://en.m.wikipedia.org/wiki/API) or the [system call interface](https://en.m.wikipedia.org/wiki/System_call).
Software was specifically crafted to fill an empty technological niche and fulfill a desired goal. Communities formed to compare and contrast methods for reaching the same end. Developers held the autonomy to make their own decisions about how the project would progress.
After using a [high-level programming language](https://en.m.wikipedia.org/wiki/Programming_language) to code a software program, it needs to be translated into [machine code](https://en.m.wikipedia.org/wiki/Machine_code). This creates the [executable program](https://en.m.wikipedia.org/wiki/Executable) to can communicate with your underlying hardware through your operating system. This process happens in multiple stages – some well in advance, while others happen [just-in-time](https://en.m.wikipedia.org/wiki/Just-in-time_compilation).
((Diagram showing compilation happening in stages, including object code, machine code and just in time))
The Windows operating system revolves around compiled programs that are easy-to-use and operate. Similarly, Linux provides access to compiled software out of the box, but also provides the source code for anyone to compile software from the ground up for their specific hardware. In practice, this can bring new life into even the oldest computer systems.
### Licensing
[Copyright](https://en.m.wikipedia.org/wiki/Copyright) grants exclusive legal rights to the originator of a creative and intellectual work – like a book, movie or software code. Relatedly, [copyleft](https://en.m.wikipedia.org/wiki/Copyleft) is a philosophy that leverages the legal protections of copyright to prioritizing sharing and collaboration.
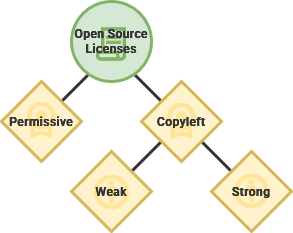
Copyleft Licenses
There are a spectrum of requirements for fulfilling the developer's intended spirit of reciprocity – from maintaining a similar software license to simply attributing through a file.
[](https://hub.subspace.services/uploads/images/gallery/2025-06/1000000534.png)
While modern "weak" copyleft licenses allow embedding within proprietary projects, the original "strong" GPL license required that the derivative project retain the same license.
|
| **Copyleft Licenses**
|
| License
| [**GPL**](https://choosealicense.com/licenses/gpl-3.0/)
*1989*
A [strong copyleft license](https://www.gnu.org/licenses/licenses.html) that comes with many conditions for usage within derivative software while providing express consent to use related patents.
|
| License | [**The Unlicense**](https://choosealicense.com/licenses/unlicense/)
*2010*
This license foregoes intellectual copyright and [attributes all work to the public domain](https://www.gnu.org/licenses/license-list.en.html#Unlicense). While not technically copyleft, this [anti-copyright](https://en.m.wikipedia.org/wiki/Anti-copyright) license is [compatible with the GNU GPL](https://www.gnu.org/licenses/gpl-faq.html#WhatDoesCompatMean).
|
| License | [**Mozilla Public License 2.0**](https://choosealicense.com/licenses/mpl-2.0/)
*2012*
This license balances the concerns of free software proponents and proprietary software developers.
|
Permissive Licenses
One of the primary differences between a copyleft license and a permissive license is the concept of "[share-alike](https://en.m.wikipedia.org/wiki/Share-alike)" – which relates to the [Creative Commons](https://en.m.wikipedia.org/wiki/Creative_Commons).
[](https://hub.subspace.services/uploads/images/gallery/2025-06/1000000533.png)
Copyleft licenses require that information about the original work is available, often creating a web of interconnected projects. Permissive licenses, on the other hand, have few stipulations on how they can be used.
|
| **Permissive Licenses**
|
| License
| [**Apache**](https://choosealicense.com/licenses/apache-2.0/)
*2004*
A permissive license that allows that this software can be incorporated into larger projects that themselves are released under a different license.
|
| License | [**MIT**](https://choosealicense.com/licenses/mit/)
*1987*
This straightforward license only requires that the licensing information is shown, otherwise the software can be used freely for any reason.
|
| License | **[BSD 4-Clause](https://choosealicense.com/licenses/bsd-4-clause/)**
*1990*
The first in a [family of permissive licenses](https://en.m.wikipedia.org/wiki/BSD_licenses) with the original requiring acknowledgement in the advertisement of all derivative works.
|
Debian codenames come from the *[Toy Story](https://en.wikipedia.org/wiki/Toy_Story_(franchise) "Toy Story (franchise)")* film universe.
[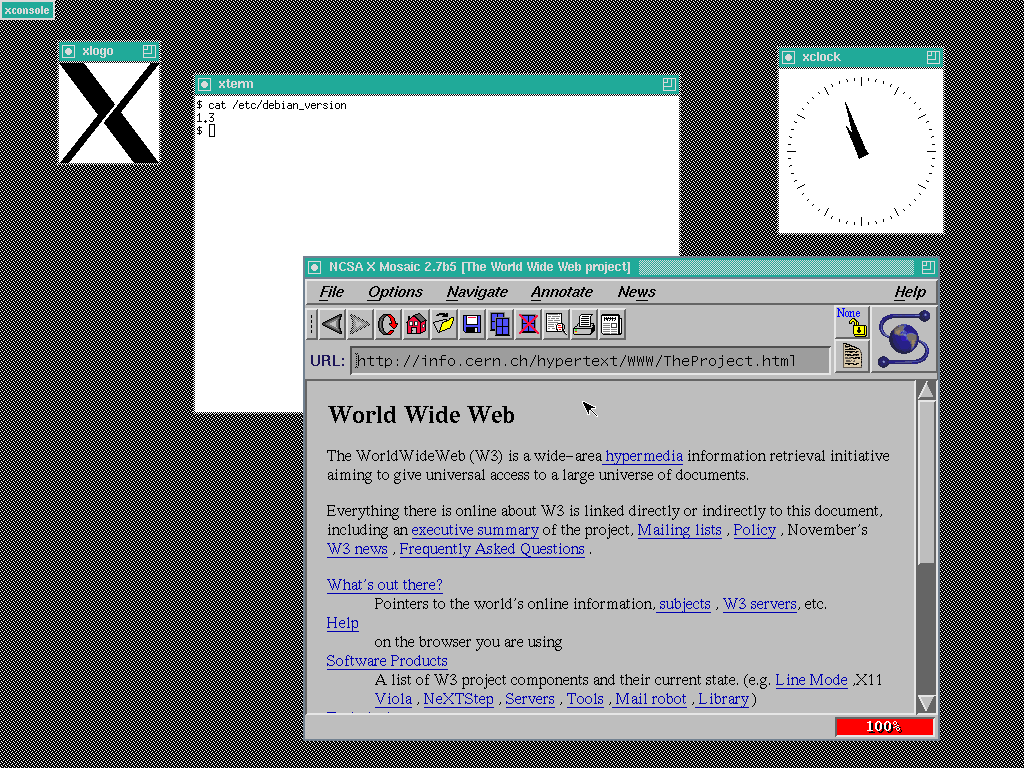](https://hub.subspace.services/uploads/images/gallery/2025-06/debian-bo.png)
*Debian v1.3 "Bo"*
Debian is a volunteer-operated software project and [accompanying non-profit organization](https://en.m.wikipedia.org/wiki/Software_in_the_Public_Interest) that operate entirely over the internet. Guided by an annually [elected leader](https://en.wikipedia.org/wiki/List_of_Debian_project_leaders), their operation is governed by three foundational documents that outline the mission and vision for their software:
| Counter\_1
| [**Social Contract**](https://lists.debian.org/debian-announce/1997/msg00017.html)
This [document](https://en.wikipedia.org/wiki/Debian_Social_Contract) outlines core principles of the project, as well as the expectations and requirements of developers who create on its behalf.
|
| Counter\_2 | [**Free Software Guidelines**](http://lists.debian.org/debian-announce/debian-announce-1997/msg00017.html)
This [document](https://en.wikipedia.org/wiki/Debian_Free_Software_Guidelines) defines "free software" and sets the requirement for software that can be used to build the operating system. While similar to the GNU Manifesto, these guidelines specifically lay out avenues for a relationship with commercial "[non-free](https://en.m.wikipedia.org/wiki/Proprietary_software)" software.
|
| Counter\_3 | [**Constitution**](http://www.debian.org/devel/constitution)
This document explores formal power structures, lying out the responsibilities of the Debian project leader and other organizational roles.
|
Debian has been developed according to principles similar to the GNU Project. In fact, they even had a [short-lived partnership](https://web.archive.org/web/20231103150337/https://www.debian.org/doc/manuals/project-history/project-history.en.txt). In contrast to the Free Software Movement, [Debian proactively included important proprietary "non-free" software](https://www.gnu.org/distros/common-distros.html) – such as firmware or drivers. Fundamentally, Debian wanted to remain open to commercial clients and the potential relationships that may follow.
At the same time, Debian was conscious of the corporate Linux distributions forming, like [SUSE](https://en.m.wikipedia.org/wiki/OpenSUSE) and [Red Hat](https://en.wikipedia.org/wiki/Red_Hat). Concerned with the potential effects that profit could have on the project's future, the Social Contract was written to ensure the operating system remained open and free.
The Four Software Freedoms were not known to the Debian project at the time.
From their perspective, the modular nature of Linux allowed people to work together despite differences in project philosophy and organization. They defined open-source software licenses that supported the spirit of the project while explicitly opening the door to commercial "non-free" software. They placed their bet on the contributions of both corporations and communities to propel mutual growth.
## Crowdsourcing Security
[Security](https://en.m.wikipedia.org/wiki/Security) can be slippery defintion that encompasses so many different things. It manifests as a [noun](https://en.m.wiktionary.org/wiki/security): in the moment, when we are safe from harm in our beds at the end of the day. It also takes shape as a [verb](https://en.m.wiktionary.org/wiki/secure): occurring over time through our proactive measures to ensure our safety. Security is [both a feeling and a reality](https://www.wired.com/2008/04/securitymatters-0403/).
We contribute to our own feeling of safety by locking the door and enacting this simple layer of security. While the locked door may be technically easy to overcome, an ongoing relationship with our neighbors and communities lends weight to this assurance. Our society frowns on the theft of property and our laws create consequences for a trespasser's actions.
Security is a mindset and an ongoing relationship, not a task or a checklist that can be completed. Protective measures shouldn't occur in isolation, but within a holistic system that values and respects security overall. We build ourselves communities who impart onto us the feeling of safety.
### Decentralized Defenses
[Cybersecurity](https://en.m.wikipedia.org/wiki/Computer_security) carries this vigilance into the digital systems we create to connect us. By using proprietary software, people must often tacitly accept the security [provided by the developers](https://www.researchgate.net/publication/3437446_Software_security_for_open-source_systems). The open-source Linux operating system approaches security in a fundamentally different way than "closed-source" ones – like Windows and MacOS.
Proprietary software rely on the concept of [security by obscurity](https://en.m.wikipedia.org/wiki/Security_through_obscurity) – the idea that it is difficult to exploit what you cannot see. This has been [proven untrue time and time again](https://csrc.nist.gov/pubs/sp/800/123/final). Without the source code available, hackers can still exploit a system but the community cannot always respond.
By contrast, the code powering Linux is openly available on the internet for review. At first thought, this may seem insecure and ill-advised – to advertise potential exploits to would-be hackers. However, a system that relies solely on obscuring vulnerability is not truly secure.
[Linus's Law](https://en.m.wikipedia.org/wiki/Linus's_law) – named after the creator of the Linux kernel – asserts that "[given enough eyeballs, all bugs are shallow](http://www.catb.org/~esr/writings/cathedral-bazaar/cathedral-bazaar/ar01s04.html)". The philosophy claims that the more independent people are working on a project, the greater the chances of uncovering bugs early. With regards to emergent "[zero-day](https://en.m.wikipedia.org/wiki/Zero-day_vulnerability)" exploits, there are numerous communities searching for the same fix.
While there have been no large-scale experiments or peer reviewed studies, [empirical evidence can offer some clues](https://arxiv.org/abs/2007.10912). Popular open-source software had a higher ratio of big fixes than less popular projects by the same company. Relatedly, [open-source GNU programs have demonstrated](https://ftp.cs.wisc.edu/pub/paradyn/technical_papers/fuzz-revisited.ps) they're [more reliable than their proprietary Unix counterparts](https://pages.cs.wisc.edu/~blbowers/fuzz-2001.pdf).
We shouldn't allow ourselves to be [lulled into false sense of security around open-source software](https://www.researchgate.net/publication/222983408_The_Open_Source_approach_-_opportunities_and_limitations_with_respect_to_security_and_privacy). Simply making source code available to a broader community does not guarantee that vulnerabilities will immediately be found and fixed. While a large community of people may use the software, [there is no promise that they are engaging](https://www.researchgate.net/publication/2955595_Open_source_security_Opportunity_or_oxymoron).
A potent illustration of this debate has been the [Heartbleed](https://en.m.wikipedia.org/wiki/Heartbleed) security bug persisting in a popular project for two years. An accidental vulnerability within [openssl](https://en.m.wikipedia.org/wiki/OpenSSL) – software that securely encrypts Internet connections – was [maintained entirely by fifteen unpaid volunteer developers](https://www.vox.com/2014/6/19/18076318/heartbleed).
> [In these cases, the eyeballs weren't really looking.](http://www.esecurityplanet.com/open-source-security/why-all-linux-security-bugs-arent-shallow.html)
>
> — [Linux Foundation](https://en.m.wikipedia.org/wiki/Linux_Foundation) Director, Jim Zemlin
### Intentional Design
Linux employs a [secure by design](https://en.m.wikipedia.org/wiki/Secure_by_design) philosophy that develops a robust architecture from the ground up with conscious planning put into design at every layer. The [Open Source Initiative](https://en.m.wikipedia.org/wiki/Open_Source_Initiative) works toward a vendor-neutral ecosystem welcoming contribution from all sectors.
Corporations and communities can lend their voices to the future of open-source software. This offers healthy competition, enabling people with choices about how to use their electronics. The Linux ecosystem has built-in support from a diversity of distributions – such as the community-supported Debian, the corporate-focused Fedora, or a hybrid-approach like Ubuntu.
[Crowdsourcing](https://en.m.wikipedia.org/wiki/Crowdsourcing) volunteers from open communities requires developers to consider how their software might be exploited from the start. By presenting source code, open communities can engage with [software review](https://en.m.wikipedia.org/wiki/Software_review) – which had been repeatedly shown to [address security issues](https://books.google.com/books?id=O3VB-zspJo4C&pg=PA154).
Despite every precaution, exploits are bound to arise within a software program – especially as the code base grows larger, including code written and maintained by other developers. By the [security company Synopsys' estimates](https://www.synopsys.com/software-integrity/resources/analyst-reports/open-source-security-risk-analysis.html?intcmp=sig-blog-ossra1), over 80% of codebases have at least one known vulnerability – on average, a codebase may have upwards of 150 vulnerailities with documented solutions available for at least two years.
[](https://hub.subspace.services/uploads/images/gallery/2025-06/1000000530.png)
The [Open-Source Security Foundation](https://en.m.wikipedia.org/wiki/Open_Source_Security_Foundation) (known as OpenSSF) is dedicated to offering security testing. Through [Security Score Cards](https://securityscorecards.dev/), developers can quickly test their software for vulnerabilities. By extension, they can advertise their rating to help build community trust with the project.
### Coordinated Response
Debian has created systems for [crowdsourcing and responding to emergent threats](https://www.debian.org/security/). They employ a [public bug tracking service](https://www.debian.org/Bugs/) that enables anyone to report inconsistencies with the operating system. Developers, researchers and [white hat hackers](https://en.m.wikipedia.org/wiki/White_hat_(computer_security)) can identify eminent threats, separating them from relatively minor programming errors.
| Bug\_report
| [**Bug**](https://en.m.wikipedia.org/wiki/Bug_(engineering))
This is a design or coding defect within a program that can lead to undesired effects – such as a crash.
|
| Skull | [**Vulnerability** ](https://en.m.wikipedia.org/wiki/Vulnerability_(computer_security))
This is a weakness in a system – sometimes the result of a bug or design flaw – that can be leveraged to compromise the security of a system.
|
| Crisis\_alert | [**Exploit** ](https://en.m.wikipedia.org/wiki/Exploit_(computer_security))
This is a procedure or program that take advantage of vulnerabilities within a system and allows a malicious actor to use it to their advantage.
|
Once threats are identified, they are assessed for severity based on technical factors – including ease-of-use and potential impact. This rating, known as the [Common Vulnerability Scoring System](https://en.wikipedia.org/wiki/Common_Vulnerabilities_and_Exposures), offers a simple 1-to-10 metric for exploit severity. Once assessed, an advisory is promptly made public with information about the exploit and any enactable defenses until the exploit is formally fixed.
[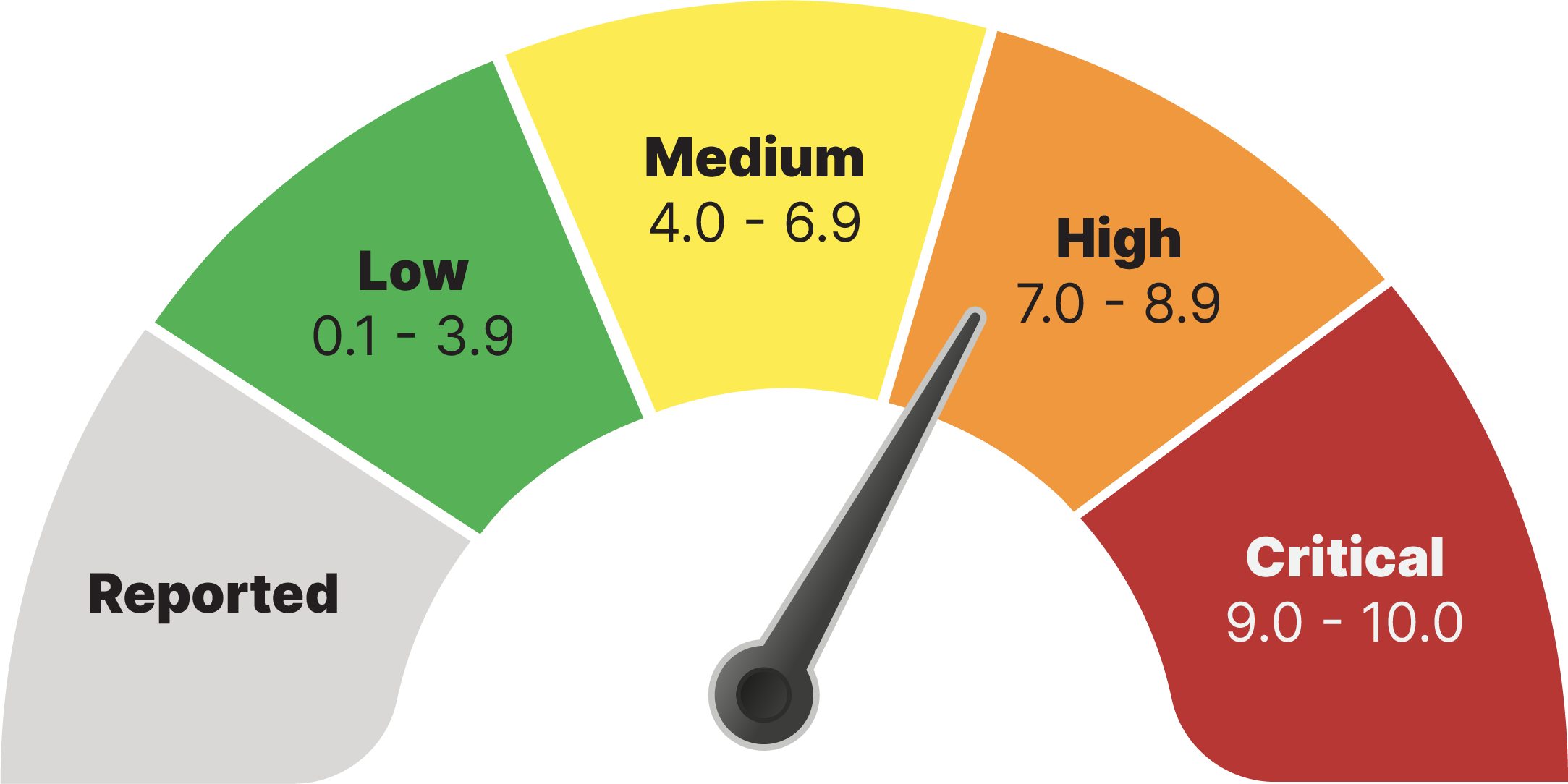](https://hub.subspace.services/uploads/images/gallery/2025-06/1000000531.png)
While an [entirely volunteer-operated organization](https://www.debian.org/intro/people), Debian hosts a [security team](https://security-team.debian.org/) who proactively ensure the security of the operating system while working with development teams to resolve critical vulnerabilities. They maintain the [documentation](http://www.debian.org/doc/user-manuals#securing) for further [hardening](https://en.wikipedia.org/wiki/Hardening_(computing)) Debian to make it even more difficult to exploit while limiting collateral.
Debian is now one of the most popular Linux distributions and many others have been created from it. As of 2025, there are [almost 140 Linux-based operating systems that rely on Debian](http://distrowatch.com/search.php?ostype=All&category=All&origin=All&basedon=Debian¬basedon=None&desktop=All&architecture=All&status=Active). It is [leveraged almost everywhere](https://www.debian.org/users/) – by governments, schools, corporations, non-profit organizations and even laptops in space aboard the [ISS](https://en.wikipedia.org/wiki/International_Space_Station). 

