Reverse Proxy
A reverse proxy is a special type of web server that forwards data from other web servers. They improve security by allowing us to keep all of our other services behind our internal network and only expose the proxy to the World Wide Web.
Secure Web Application Gateway – more commonly referred to SWAG – is a community-driven project by LinuxServer.io to host an nginx server.
nginx
We will be using this as a reverse proxy to manage provide access to our individual services through a centralized location.
{{Show difference between reverse proxy and connecting individual services to the internet.}}
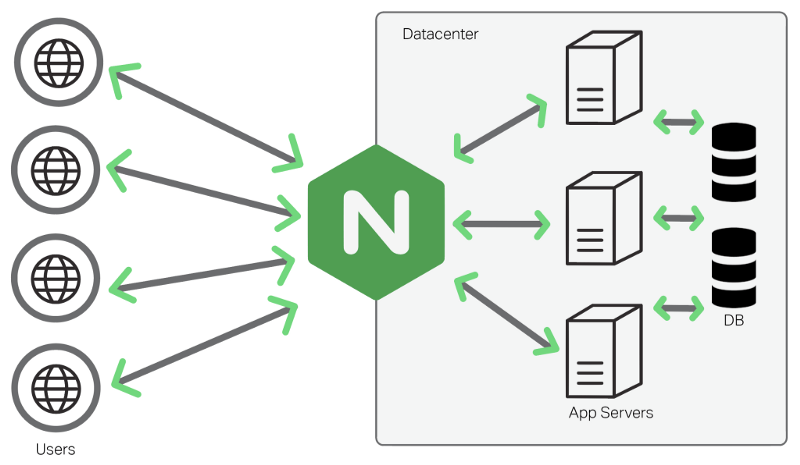
Nginx ("engine x") is an open-source Web server, reverse proxy and load balancer that is used to power the majority of corporate domains. Nginx can be used to host a standard HTTP(S) Web server with PHP functionality and add-on modules. It can also be used as a reverse proxy which acts as the "public face" of that domain. It acts as an intermediate server that receives client requests and forwards that data along to another server behind the scenes.
This increases security by keeping the majority of data transmission on your local network and only forwarding data as requested. Instead of routing services directly to the internet, a reverse proxy acts as a central access point to increase the attack surface and isolate other servers from the world wide web. This also provides a centralized location to cut server access in the event of emergency.
When hosting larger infrastructure with multiple servers hosting the same website to be accessible to thousands of people, a Load balancer can be used to ensure that traffic is split between the servers evenly so that everyone gets an equitable experience.
Show different servers with users and show a request going to the least populated
Secure Web Application Gateway – more commonly referred to SWAG – is a community-driven project by LinuxServer.io to host an nginx server.
We will be using this as a reverse proxy to manage provide access to our individual services through a centralized location.
{{Diagram of Cockpit on a server being linked through a relay server to outside internet}}
We are hosting Docker services on our server with access to their web interface linked to local ports. This is how we can access Cockpit through a Web browser from computers on our local network. By using a reverse proxy, we can route access to Cockpit through a web sub-domain – such as cockpit.example.com.
It is recommended that services like Cockpit are restricted to Local Area Network access.
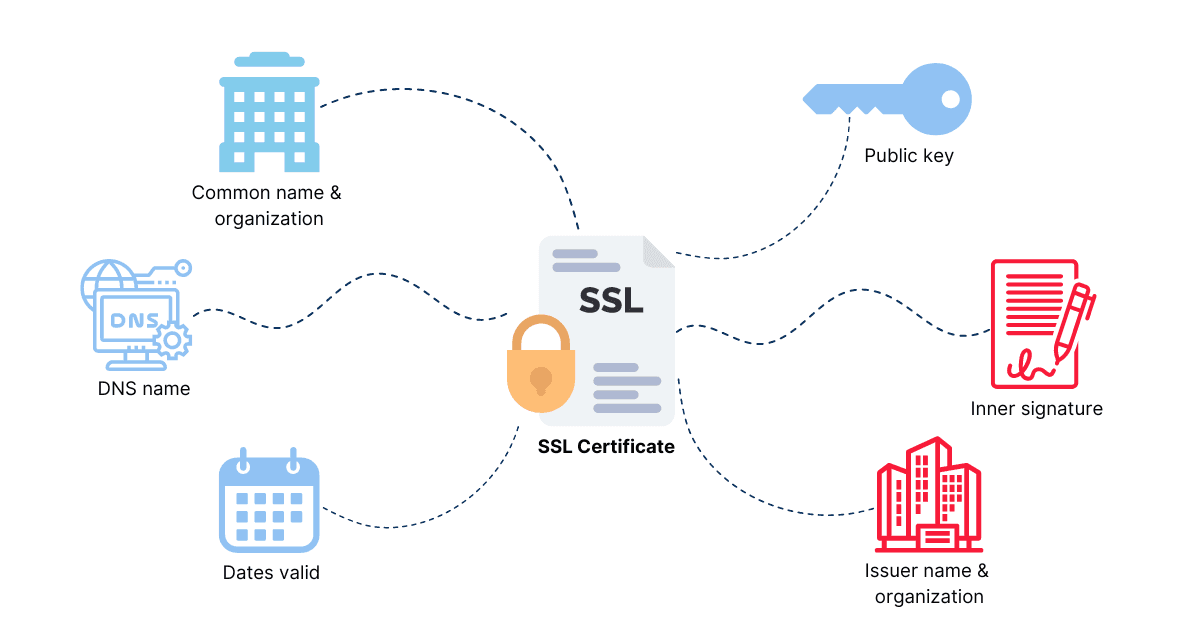
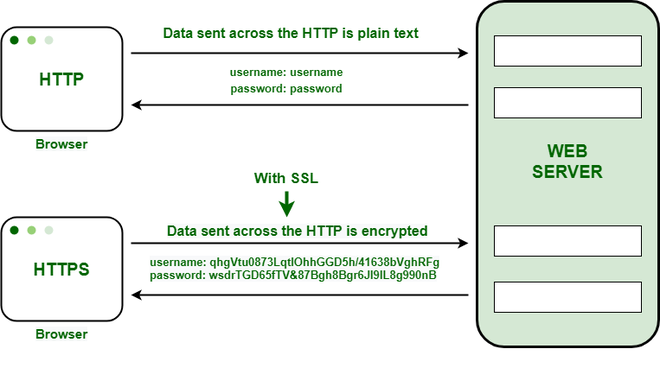
SWAG makes it easy to automatically generate an SSL certificate using a variety of mechanisms. These form the foundation of the HTTPS protocol by verifying the identity of the server and encrypting data sent through a secure TCP connection.
SWAG also provides preconfigured settings for integration with other security-focused add-ons:
|
Dashboard |
This provides a graphical overview of the common device types, geographical regions and IP addresses accessing your SWAG reverse proxy server. |
| Front_hand |
This software offers intrusion detection that blocks malicious IP addresses that repeatedly fail authentication checks for your services. |
| Verified_user |
An open-source authorization portal that offers single sign-on and two-factor authentication for securing accessing your services. |
| Communities |
This projects offers proactive threat protection by fostering an open community to share information about malicious Internet actors. |
SWAG comes bundled with accessible default options that balance security and convenience. This also includes templates for each ofthe services you are making available. This will require first configuring and installing the software through Docker Compose using Portainer.
Preparation
There are some things we need to do in preparation to install this service.
Volumes
Persistent Data
This is where the service will store its own application data and ensures we can quickly update the service image.
Ensure your user has permissions to access the folder.
Media Folders
This service will need access to the folders where you store your media files.
Ensure your user has permissions to access the folder.
Download Folders
This service will need access to the folder where you torrent or usenet folder store their completed downloads.
Ensure your user has permissions to access the folder.
Environment
You can find available Environmental Variables in their documentation.
PUID
This is the numeric ID of the user account on Debian. If you are unsure, open a terminal and run:
id -uPGID
This is the numeric ID of the user account's group on Debian. If you are unsure, open a terminal and run:
id -gPasswords
Keep these securely stored in a password manager, such as VaultWarden.
DB_ROOT_PASS
This is the password that will be used for root access to the database.
It is important to use secure, randomly generated password.
You can use a random alphanumeric string from a password manager, or open the terminal and run the command:
tr -dc 'A-Za-z0-9!"#$%&'\''()*+,-./:;<=>?@[\]^_`{|}~' </dev/urandom | head -c 32; echoThis pulls a random string from the 'urandom' device, removes unwanted characters and trim it to an appropriate length.
OWNCLOUD_ADMIN_PASSWORD
This is the password for the administrator account that will be used within the web interface.
It is important to use secure passphrase that is easy-to-remember.
Installation
The service can be installed through the Portainer web interface.
Learn about creating a new stack.
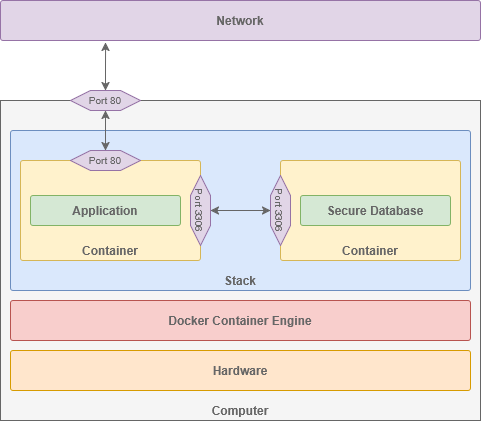
Overview
Before we install this service, we should understand the basic layout and connectivity of the Docker stack we will be creating.
Docker Compose
Use the following code to install the service:
---
services:
actual-server:
image: docker.io/actualbudget/actual-server:latest
container_name: actual-server
network_mode: bridge
environment:
- TZ=America/Vancouver
volumes:
# Persistent Data
- /srv/actual-budget:/data
ports:
- 5006:5006
restart: unless-stoppedEnvironment
Use the following environment to configure the service using the values prepared earlier:
TZ=America/Vancouver