Reverse Proxy
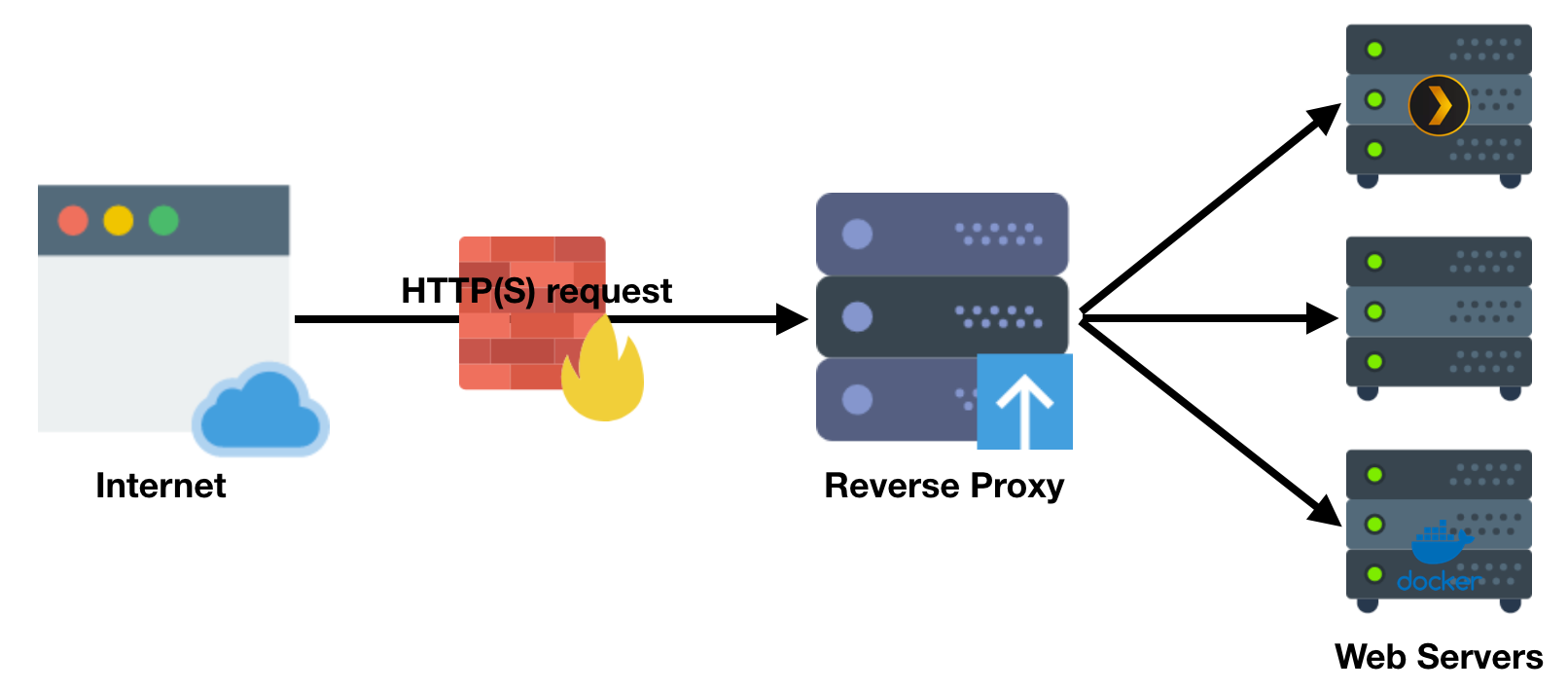
ToWe need to install a reverse proxy in order to safely access our web server over the World Wide Web, we need to install a reverse proxy. Web. This specialized webserver serversoftware sits in front of other servers so they can retrieve a websites on behalf of client accessing them. For example, accessing this website is retrieving data from another server behind-the-scenes. When passing along web site data, a reverse proxy will actively overwrite any other datainformation about wherethe server it came from. This also enables our server to modify data and configure it's appearance from the top-down.
This lets us keep access to our services behind the privacy of our Local Area Network and ensures clientsno one can neverever communicate directly with anyan origin server. This decreases our attack surface – and improves security – by only giving World Wide Web access to the reverse proxy instead of by individual service. In the event our server is compromised, they only gain access to the reverse proxy and not any of our underlying services.
{{Show difference between reverse proxy and connecting individual services to the internet.}}
Within cloud computing environments, reverse proxies alaoalso provide powerful speed benefits.
on
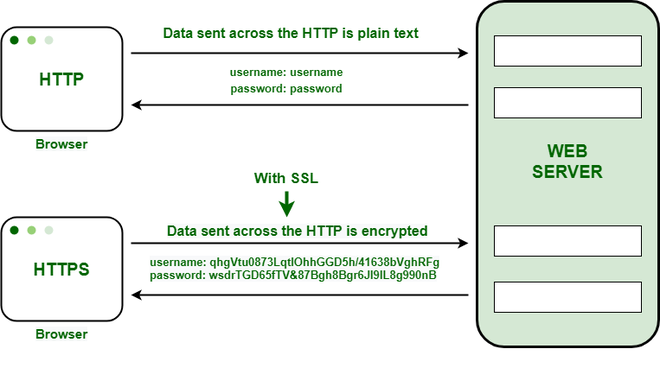
multipleCacheSSL encryptionActing -as Encryptinga andcache decrypting– SSL (or TLS)a communicationscopy forof eachfrequently clientrequested candata be– computationally expensive for an origin server. Aa reverse proxy can bestep configured to decrypt all incoming requestsin and encrypt all outgoing responses, freeing up valuable resources ontake the originstrain server.Theyoff of individual services by handling simple requests. This data can also allow you to modify unencrypted Web traffic from proxies behind the scene – this can be anythingcompressed fromso allowingthat thethere appis less that that needs to be embeddedtransmitted inover anthe iframeinternet.
Encrypting data for secure transmission over the open internet using SSL can require a great deal of hardware resources. This is where a reverse proxy become indispensable because they can handle the encryption (and decryption) of secure data with clients outside of the Local Area Network. This enables secure internal communication between server – even without needing to addingencrypt scriptsit.
A compromised reservereverse proxy canhas the potential to cause a lotgreat deal of damage and they should be safeguarded.A reverse proxy can be used to compress data before it is sent out and can be helpful for a personal server with data restrictions.
By acting as the singular access point for a plethora of behind-the-scenes services, a reverse proxythey can also represent a single point of failure where a single malfunction can leave you without any access. This is a contingency that we prepared for by setting up local network access protocols, but it might be prudent to operate your web server in a place where you can access a mouse and keyboard.
nginx
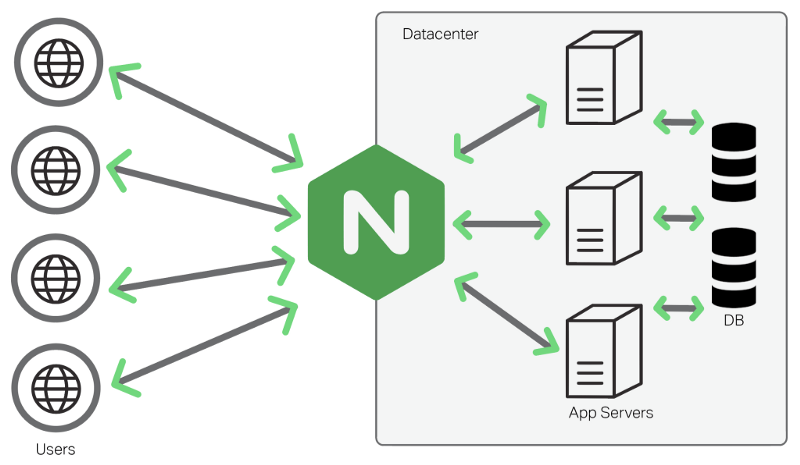
Nginx ("engine x") is an open-source WebHTTP server, reverse proxy and load balancer that is used to power the majority of corporate domains.
Nginx can be used to host a standard HTTP(S) Web server with PHP functionality and add-on modules. It can also be used as a reverse proxy which acts as the "public face" of that domain. It acts as an intermediate server that receives client requests and forwards that data along to another server behind the scenes.
Secure Web Application Gateway
Secure Web Application Gateway – more commonly referred to SWAG – is a community-driven project by LinuxServer.io to host an nginx server. We will be using this as a reverse proxy to manage provide access to our individual services through a centralized location.
In this case, a user or a client browser can connect to our SWAG container via https on port 443, request a service such as Ombi, then our SWAG container connects to the ombi container, retrieves the data and passes it on to the client via https with our trusted cert. The connection to ombi is local and does not need to be encrypted, but all communication between our SWAG container and the client browser will be encrypted.
We are hosting Docker services on our server with access to their web interface linked to local ports. This is how we can access Cockpit through a Web browser from computers on our local network. By using a reverse proxy, we can route access to Cockpit through a web sub-domain – such as cockpit.example.com.
{{Diagram of Cockpit on a server being linked through a relay server to outside internet}}
It is recommended that services like Cockpit are restricted to Local Area Network access.
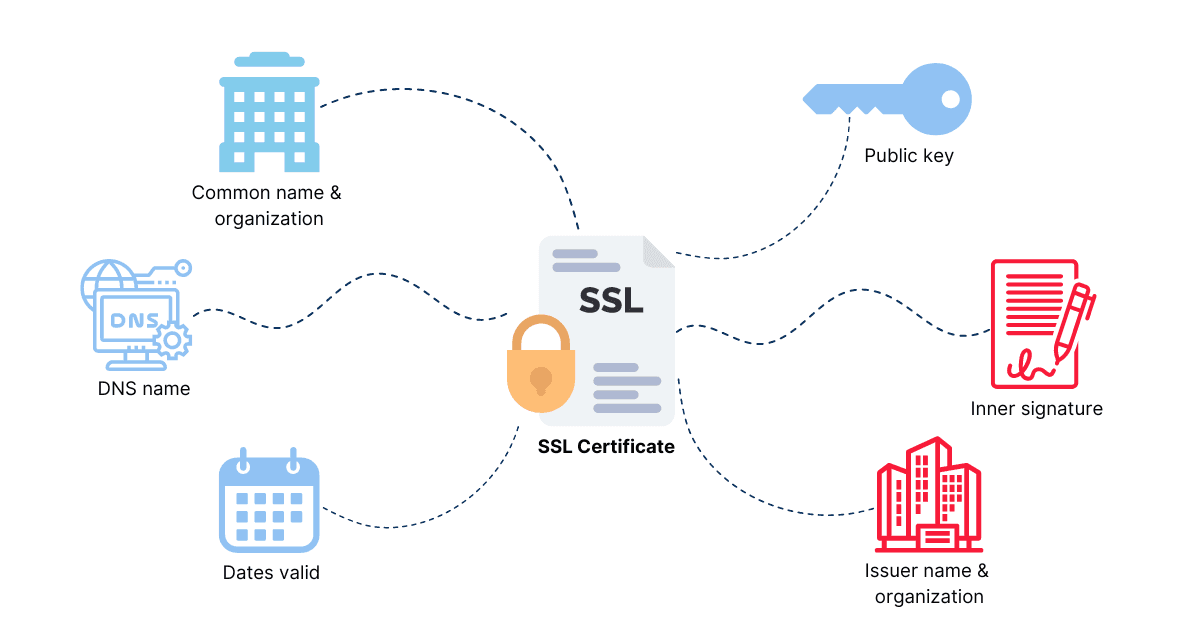
SWAG makes it easy to automatically generate an SSL certificate using a variety of mechanisms. These form the foundation of the HTTPS protocol by verifying the identity of the server and encrypting data sent through a secure TCP connection.
SWAG also provides preconfigured settings for integration with other security-focused add-ons:
|
Dashboard |
This provides a graphical overview of the common device types, geographical regions and IP addresses accessing your SWAG reverse proxy server. |
| Front_hand |
This software offers intrusion detection that blocks malicious IP addresses that repeatedly fail authentication checks for your services. |
| Verified_user |
An open-source authorization portal that offers single sign-on and two-factor authentication for securing accessing your services. |
| Communities |
This projects offers proactive threat protection by fostering an open community to share information about malicious Internet actors. |
Add Geo-Blocking
SWAG comes bundled with accessible default options that balance security and convenience. This also includes templates for each ofthe services you are making available. This will require first configuring and installing the software through Docker Compose using Portainer.
Swag also operates as a basic Web server, serving a site at both port 80 and 443. It does not include any proxy configuration by default and instead serves a basic HTML website that can be currently be accessed on your local network.