What are Computer Networks?
Computer networking refers to computing devices and the interconnected relationships between them that are used to transmit data. These networks are based on standards that allow physically distant devices to communicate with each other.
The Path of Data
Data can travel over vast distances to get from it's origin to it's final destination. This can include multiple internet service providers and internet connection types – ranging from physical connections like Cable and Fiber Internet, to wireless connections like Satellite or fixed community internet. This can even include vast underwater cable networks for carrying data.
After data is broken into pieces by your desktop computer, it is transmitted to your router. From here your data transitions from your private to public IP. Your data is transmitted across the infrastructure laid by your internet service provider to a local hub and then, possibly, your ISPs central hub.
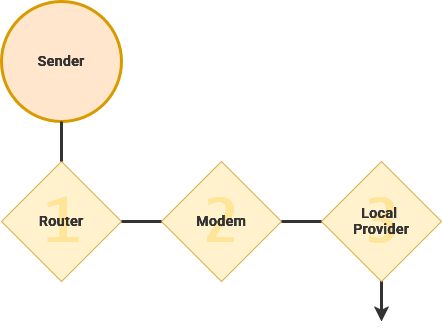
Your ISP contracts for access and bandwidth to a long-haul provider that specialize in quickly transmitting data between local ISPs across a geographical region. For example, within north America, some notable long haul providers are Verizon and AT&T.
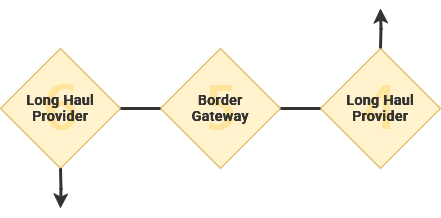
Through the Border Gateway Protocol, long haul providers and small local ISPs alike can find a route across this patchwork of Wide Area Networks. If individual packets of information contain any erroneous or fabricated metadata, they may get lost in transit during this transfer.
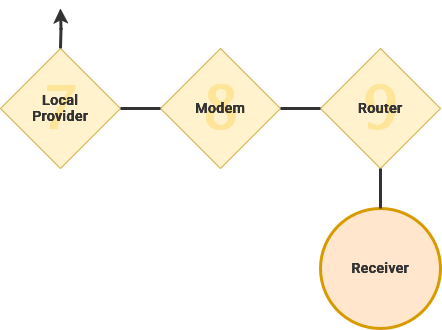
From here, data will attempt to take the most direct route to it's destination. Performing the same process in reverse, the data will transit to regional long haul providers, to local ISPs, their router and the intender device. If you have ever taken a transfer flight, you can understand how a direct route can become pretty circuitous.
Connected Collectives
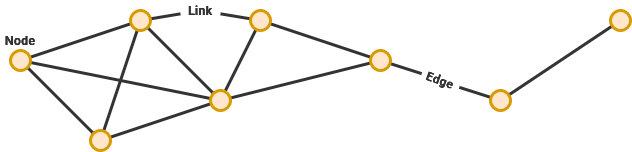
Computer networks consist of nodes – which are devices that are seeking to communicate – as well as links – or the connections between each node. Nodes are often connected to other nearby nodes, creating a complex mesh that messages can traverse. Occasionally, small edge networks can form around internet connectivity bottlenecks that arise in rural, disconnected areas that require satellite or single entry points.
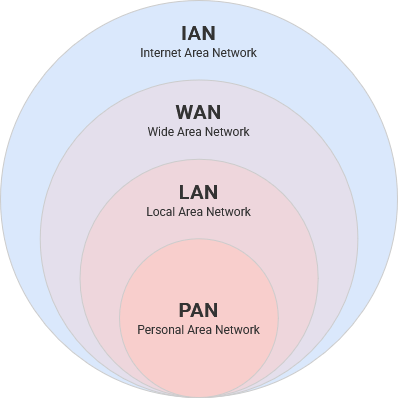
When your phone is connected to your headphones through bluetooth, you are creating a Personal Area Network, or PAN.
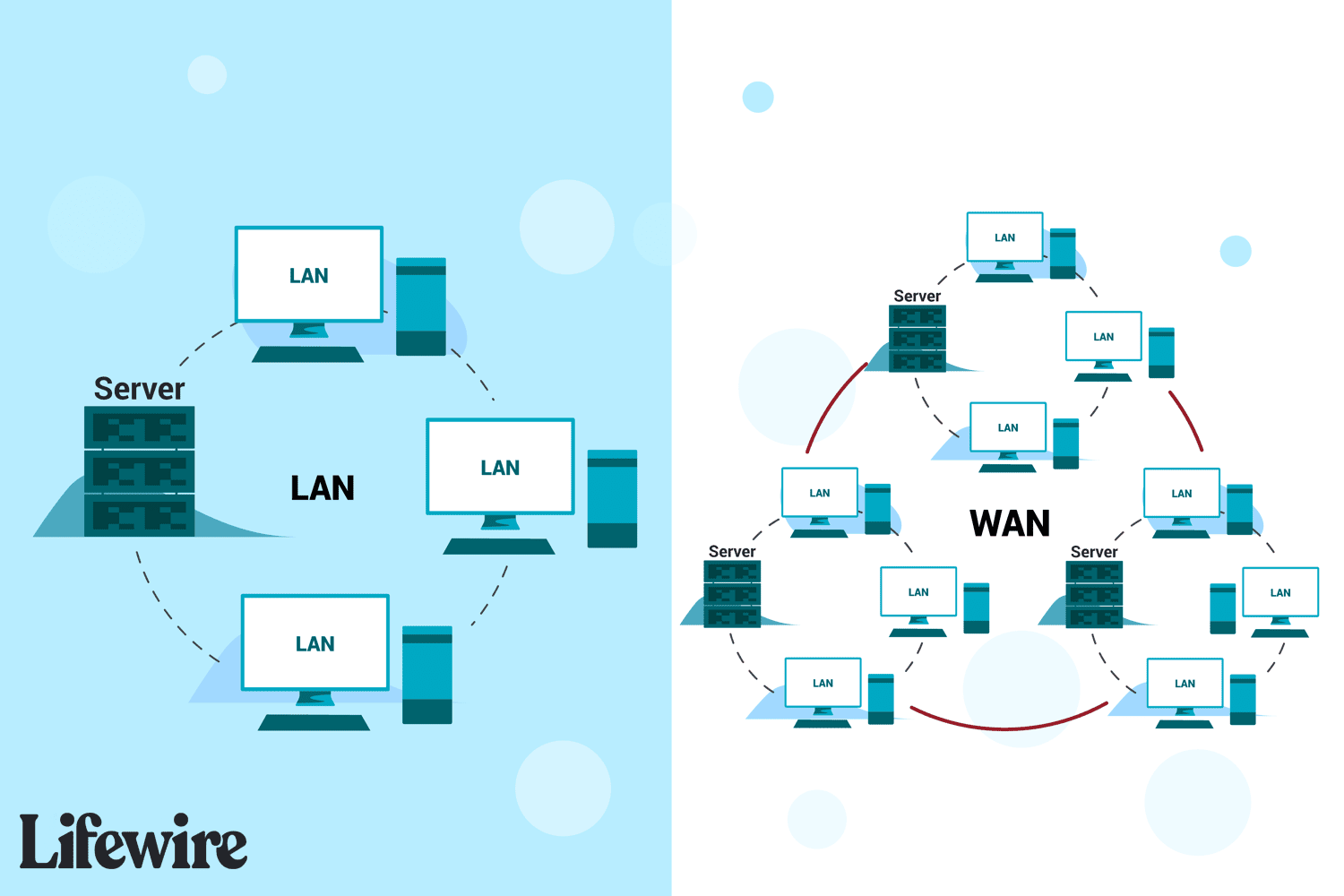
A local area network, or a LAN, are the nodes and links within a limited area, such as your home or perhaps even a larger area like a school campus.
For example, your phone, laptop, desktop and television are connected to your home's LAN. These are generally behind a modem provided by an internet service provider and provide a layer of security, isolating your network from your neighbors network.
At school or work, your phone connects to one router that is connected to a mesh network of other routers, creating one single lan spanning multiple buildings. Just like you, they subscribe to an internet service provider – just on a larger scale.
Local Area Networks
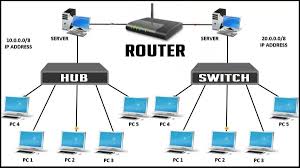
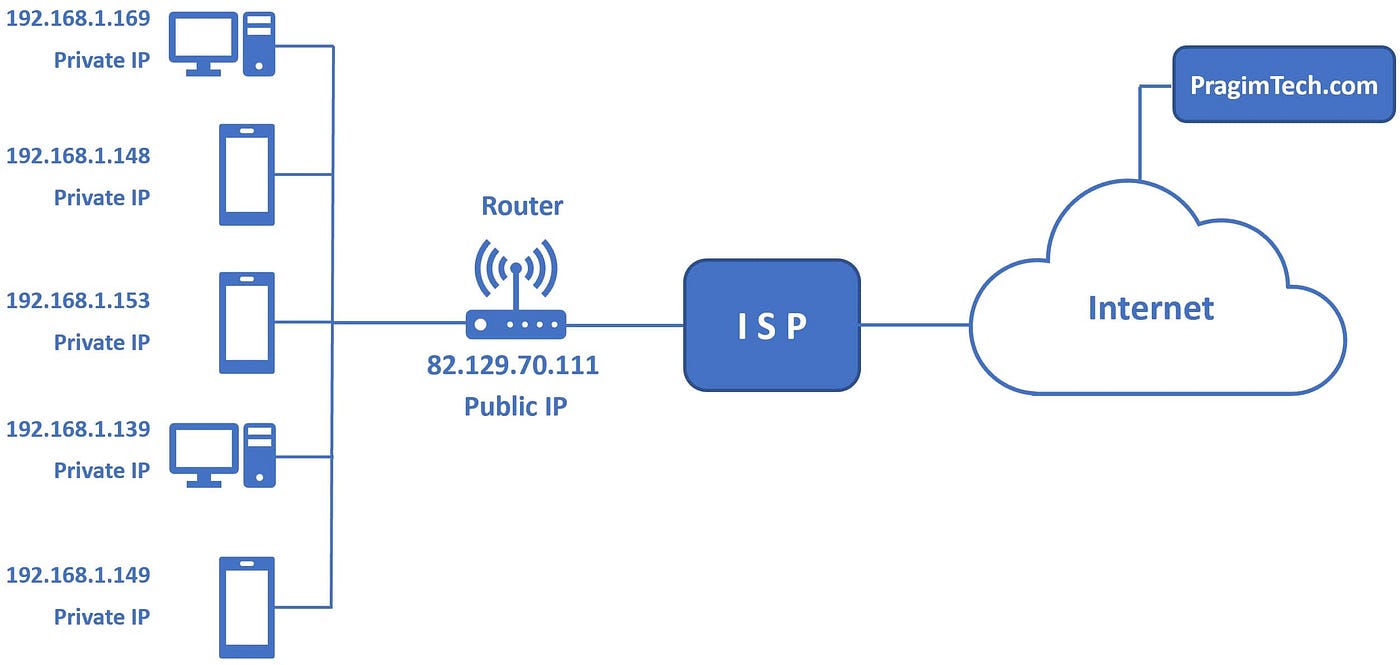
Within your local area network, all of your devices connect to your local router – sometimes provided by your ISP. Within this local network, powered by your router, your devices are given a unique numerical identifier known as an IP – or internet protocol – address. For example, this might look like 192.168.68.250. This number allows us to designate over a network of multiple computers, which one we are specifically trying to speak to. There are three "reserved" IP address ranges for local networks: 10.0.0.0, 172.16.0.0, 192.168.0.0. Your local router – tasked with assigning IP addresses to everyone – acts as a gateway for all of the devices on your network to the Internet.
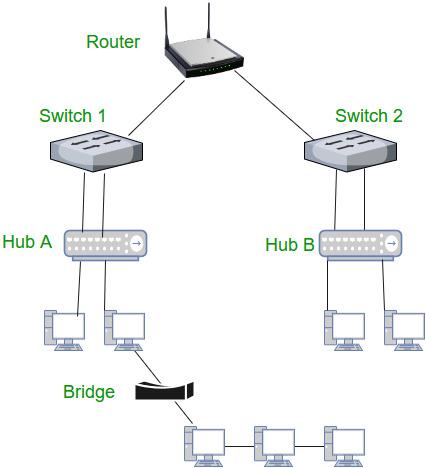
When connecting devices on a local network, a few types of networking devices can be used. The router orchestrates communication between all the devices connected to it, while hubs and switches can create smaller subnetworks. These can be put together in many different configurations to achieve the desired efdect or reach specific requirements. Judging solely by appearance, it can hard to tell them apart.
|
Router |
Hub |
Switch |
A hub can connect many devices to the network, but it openly broadcasts all data it receives to every device connected to it. This can be cost effective because they are based on simple circuits, but increase the potential for snooping and decrease overall performance.
A switch is more intelligent and will only send data to it's intended recipient. This require more powerful , and expensive, internal hardware to process the information being transmitted through it. This ultimately results in higher performance and better regulated security.
Wide Area Network
Individual LANs, such as your network – as well as your neighbors, city, county and state – are conglomerated together into a Wide Area Network or WAN. Your router, acting as the gateway for your devices to the internet, is also assigned a Wide Area Network IP Address. For example, the IP address for example.com is "92.122.244.34" allowing anyone in the world to know exactly how to locate the web server over the internet.
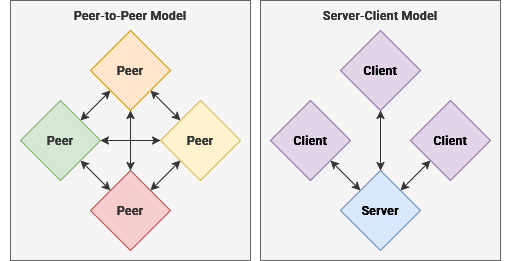
VPN connecting two lan over the internet to create a secure, private and enceyoted tunnel for all data between the two, allowing them to operating as one Lan. A computer can act either as a server - that broadcasts the service - or a client that connects to it.
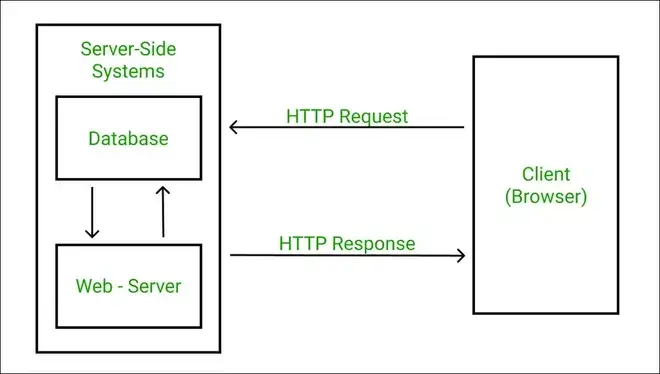
The modern internet, as we know it, predominately operates within the sever-client model. This means that one computer – a server – is used to respond to the requests of other computers – known as clients.
When visiting a web url, such as example.com, it is converted to an IP address of a server by the DNS. By connecting to this IP address through your web browser, you can access the website that is being served to clients. Peer-to-Peer networks, where each computer acts as both a server and a client, are becoming more popular for services like BitTorrent, OwnCloud and Social Media.
DNS
Domain names
Open Standards
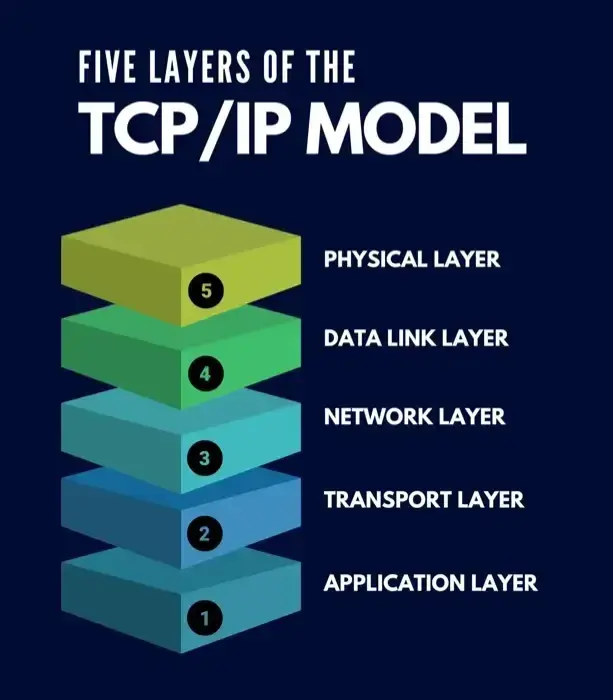
Data transmission over the internet is built upon a technology first explored in 1960s with ARPANET. By the 1980s, the standard for communication over the internet – known as TCP/IP or more commonly the Internet Protocol Suite – was first implemented. Simplified, access over the internet is broken into four alayers:
Each of these layers provide standards for how to ensure each layer can communicate with other devices through this protocol. At each level, we are ensuring that all nodes on the network are speaking a common language.
- Physical Layer: This layer handles how data signal is encoded and physically transmitted over wires. This layer can function in different ways, depending on your internet connection type – such as internet over coaxial cable or fiber optic cable.
- Link Layer: This layer handles how data is transmitted over the network through physical hardware such as Network Cards and Ethernet cables. This also includes hardware level identification of devices on the network, through a MAC Address, that allows the router to know which device is which, even when it hasn't been previously connected before.
- Network Layer: This layer dictates how nodes can find each other across the network, utilizing IP addresses and routing to determine how to get from point A to point B. This is the layer where devices are provided IP addresses on their local and wide area networks, and traces the optimal route between two nodes using these IP addresses. Data transmitted over this layer is broken up into small segments that are easier to transmit. TCP and UDP.
- Transport Layer: This layer is responsible for ensuring that individual nodes can communicate with each other reliably and without errors. Now that data is broken up into small segments for transmission, we can chose to transport this data in different ways.
- Application Layer: This is the top most layer of the internet where protocols such as HTTP and SMTP are implemented. This is the layer that most people interact with when they are browsing the internet through operating system applications. At this level, the user doesn't need to consider how or where the data is traveling. It happens almost invisibly.
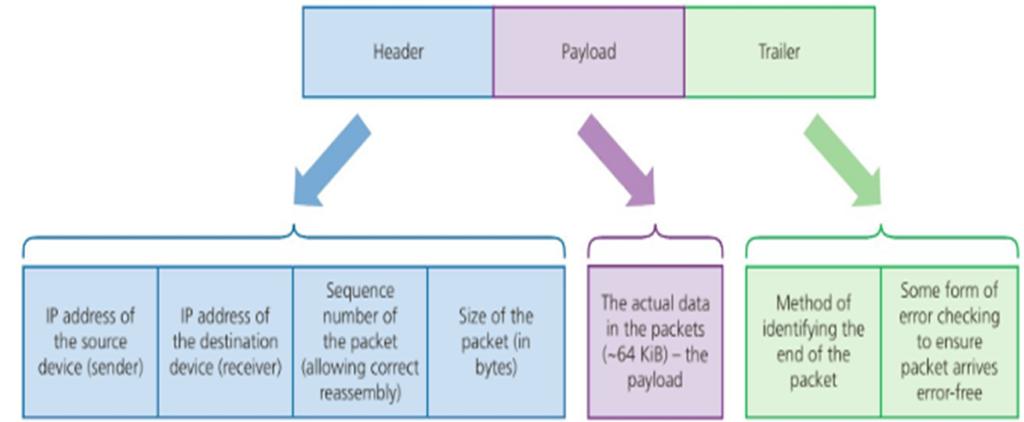
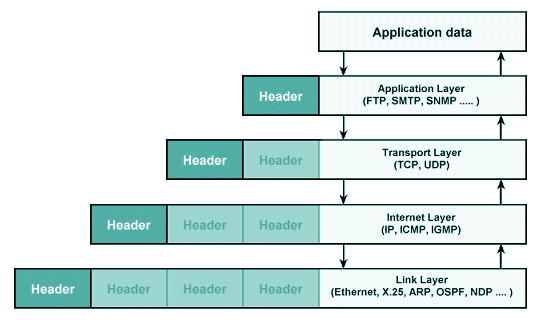
In between each layer, as our data transmission is broken into smaller and smaller pieces by our physical device and the software installed on it, "metadata" is appended to each small packet. These "headers" detail how this packet of data relates to other packets, as well as the path taken and route still in progress.
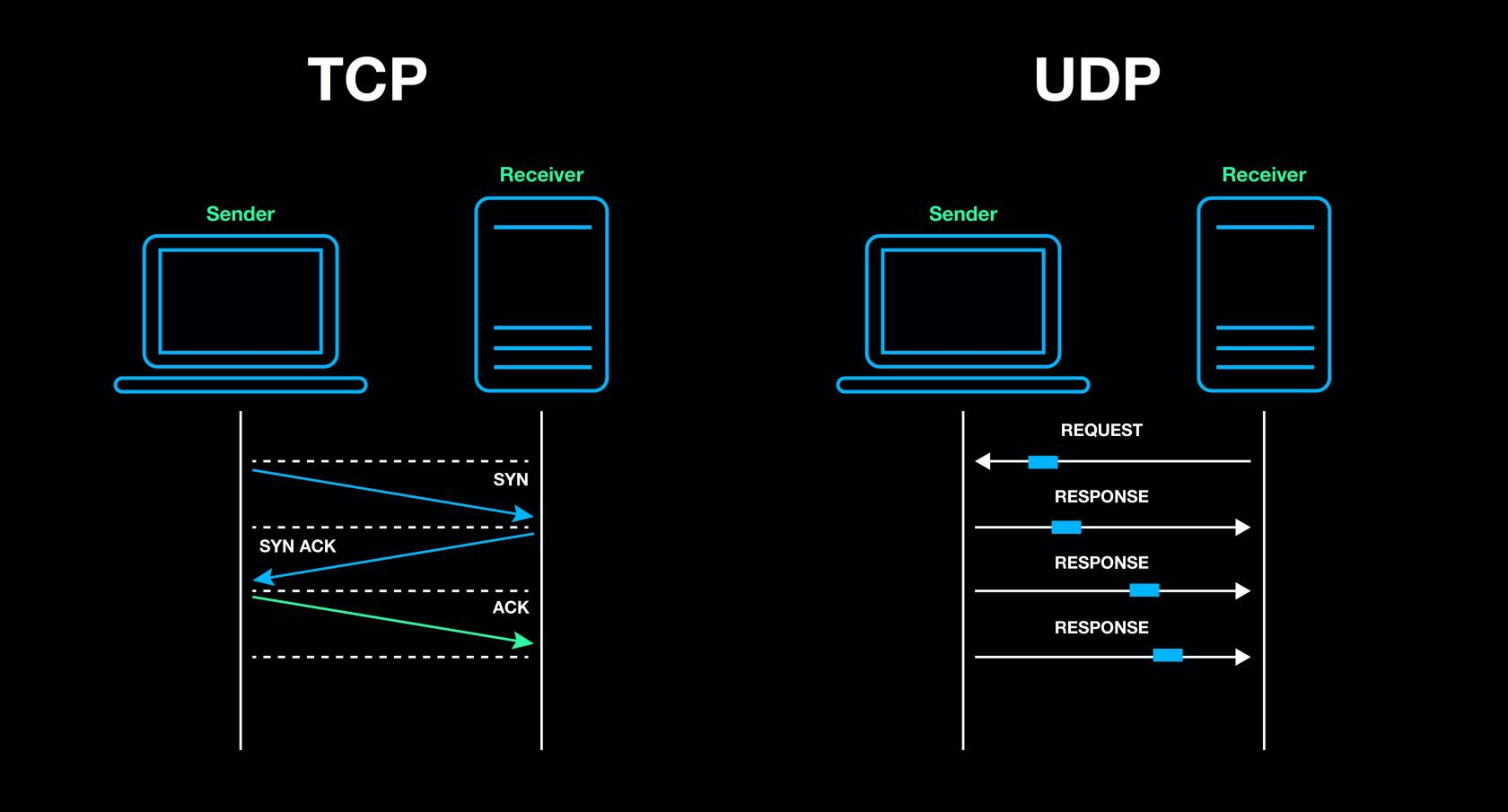
Once two nodes on a network have initiated communication - such as your laptop connecting to a remote server – through the internet later by up address, they need to confirm the method for communication. When developers design an application, they can choose to transmit data over the internet through two protocols, both with benefits and drawbacks.
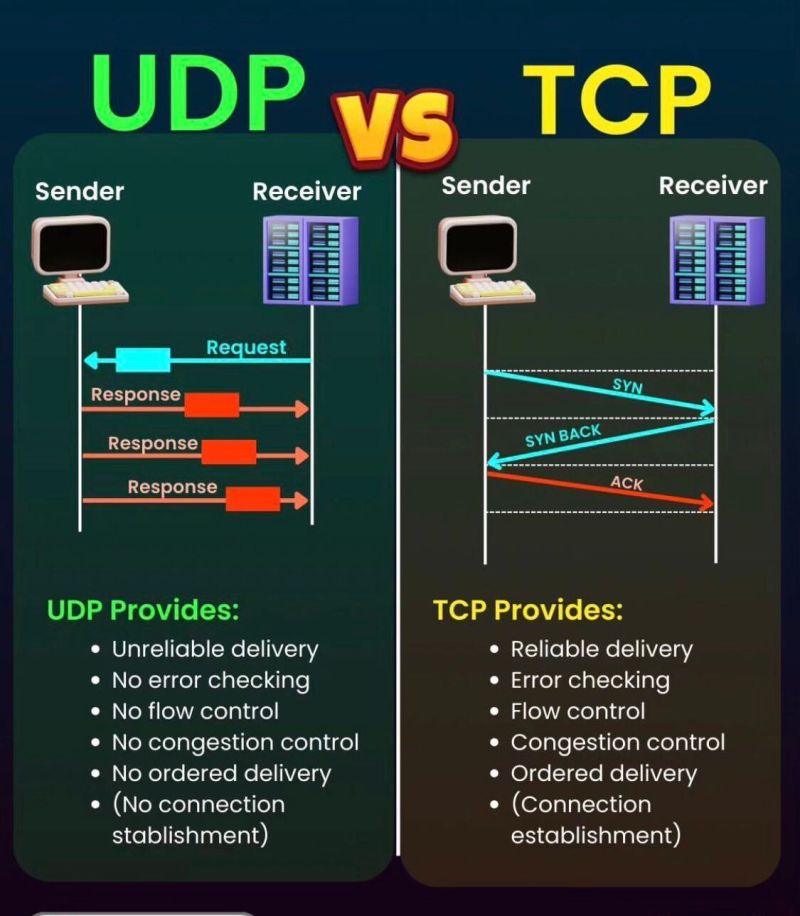
TCP ensures that all data will arrive with perfect fidelity and in the current order. In order to do this, both devices need to "handshake" – or agree to initiate a data connection between them. Packet 1 will be received before Packet 2, and so on. Each data packet is individually verified to ensure it was received correctly and, if it isn't, it is transmitted again and again until it is properly received. This is more process intensive and can take longer because it transmits one packet at a time. This protocol is used for HTTP, the backbone of the world wide web, and TLS, which encrypts web traffic and verifies the identities of all nodes.
UDP, on the other hand, allows a client to begin rapidly sending data to a server without first needing to "handshake". Packets can be transmitted in parallel, meaning that the server will not receive data in any particular order or within a specific time frame. Packet 2 could be received first, followed by 1 and 3. In the event that a packet is never received or fails basic integrity checks, the server is made aware of the error but the data is never transmitted again. This is more common for time-sensitive applications, online video games or live streaming services because it may be preferable to risk losing data then it is to receive it late.
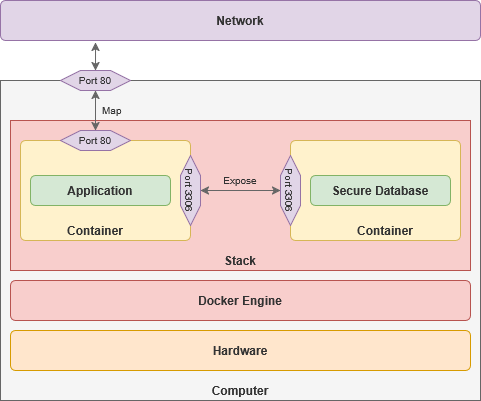
Ports: software-based channels that allow multiple services to exist on one computer. They also allow them to communicate over a local network with great complexity and versatility, without needing a domain name. This allows services to communicate behind the scenes, away from the internet. These ports are also often reserved for specific protocols, such as HTTP, HTTPS, SSH and DNS.