What are Computer Networks?
We use the internet everyday, but it isn't often – if ever – that we need to consider how it works. That's because the protocols powering the internet were intentionally designed to operate as invisibly as possible. Built around a common language, networks enable devices to communicate with each other and share resources. By standardizing how computers talk with each other, we have expanded the scale of networks over time seeking to achieve a global cloud infrastructure.
Connected Communities
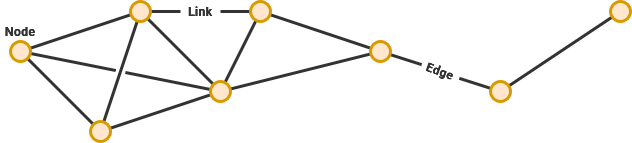
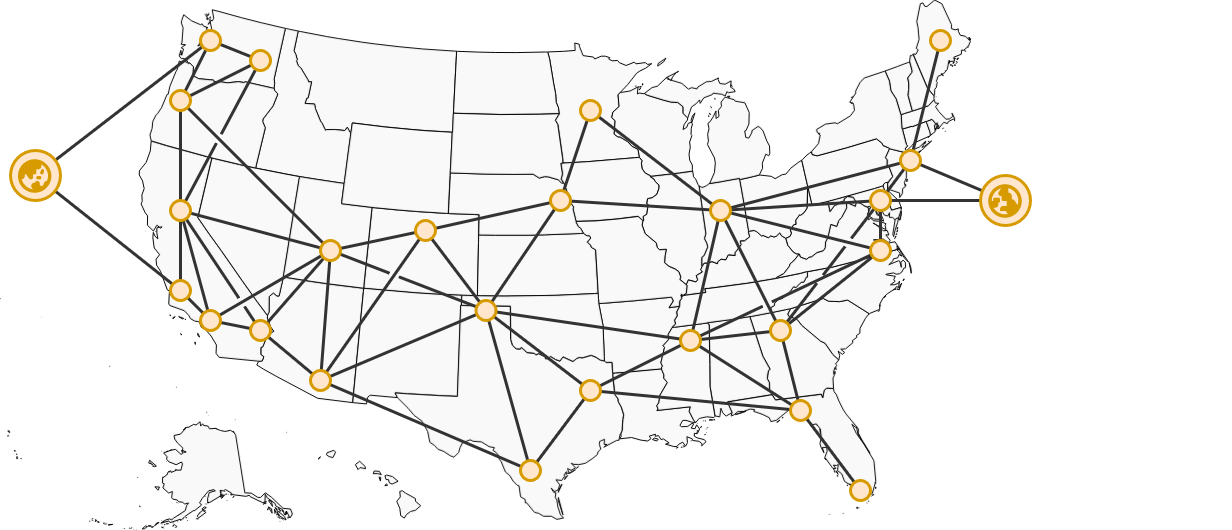
Computer networks consist of nodes – which are devices that are seeking to communicate – as well as the links between them. Under some circumstances, nodes will connected to other nearby nodes and creating a mesh that data can traverse along while seeking it's destination.
Occasionally, edge networks form around internet connectivity bottlenecks that arise in rural, disconnected areas. This can increase the cost of internet service, as well as effect the overall speed or availability of internet access. These often arise along geological boundaries – such as mountains – as well as within marginalized and disconnected communities.
What areas are disconnected? Why might that be?
Networks, similar to much of computing, relies on abstraction to allow people to comprehend the scale of electronics required to power computers at this scale. In order to build a global infrastructure, digital technologies have created a stratified system that simplifies data shared in between these layers. You don't need to understand electrical engineering to build a computer system. Similarly, data isn't concerned about the path it takes – just that it has one.
Show a hypothetical PNW local map
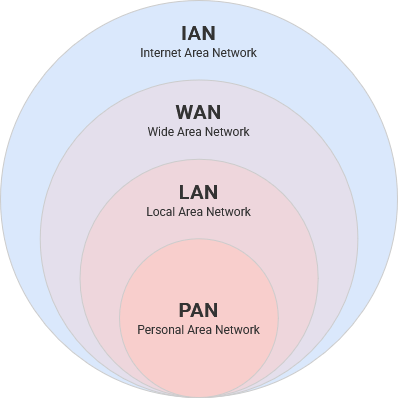
When your phone is connected to your headphones through bluetooth, you are creating a Personal Area Network, or PAN.
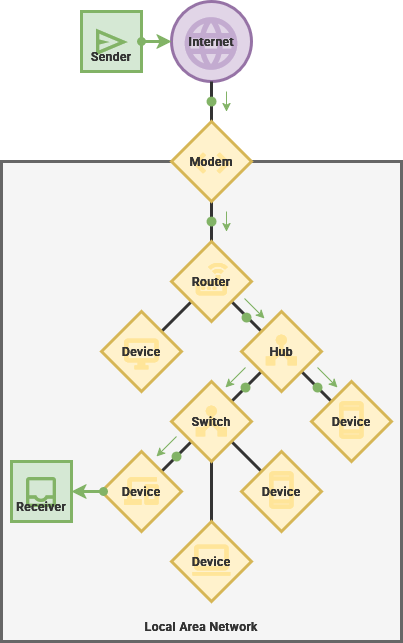
A local area network, or a LAN, are the nodes and links within a limited area, such as your home or perhaps even a larger area like a school campus.
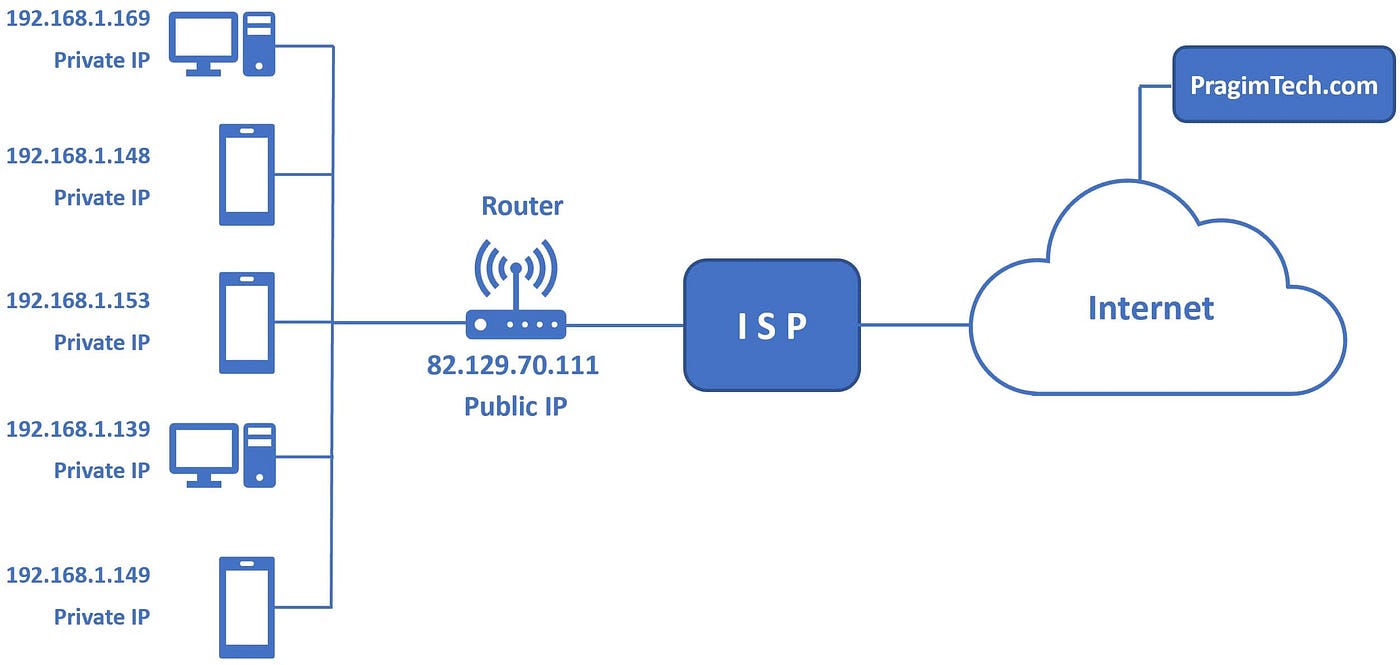
From here your data transitions from your private to public IP.
https://personalpages.manchester.ac.uk/staff/m.dodge/cybergeography/atlas/more_isp_maps.html
For example, your phone, laptop, desktop and television are connected to your home's LAN. These are generally behind a modem provided by an internet service provider and provide a layer of security, isolating your network from your neighbors network.
At school or work, your phone connects to one router that is connected to a mesh network of other routers, creating one single lan spanning multiple buildings. Just like you, they subscribe to an internet service provider – just on a larger scale.
The Path of Data
Data may need to travel vast distances to get from it's origin to final destination. This can include multiple internet service providers and connection types – ranging from physical cables to wireless connections. Carrying data around the globe can include anything from vast underwater cable networks to satellite relays in geostationary orbit.
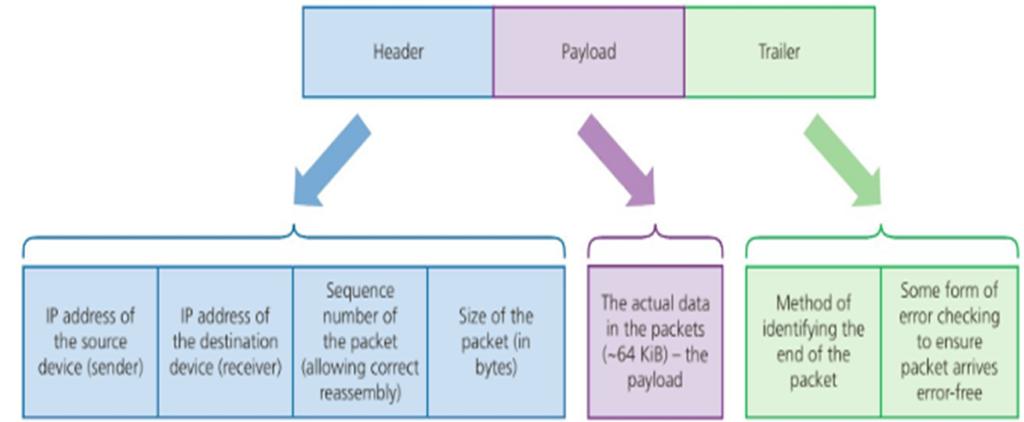
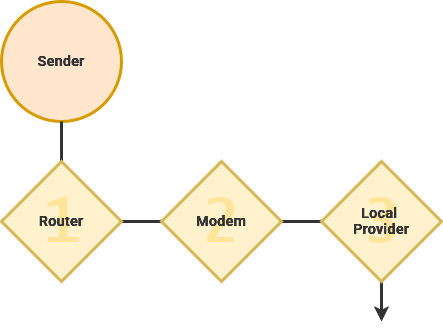
Whenever data is transmitted over a network, it is first broken into small "packets" by your computer. These are transmitted to the network router and across the infrastructure laid by your Internet Service Provider to youra local hub and, possibly, a regional or central hub operated by your Provider.
Your Provider contracts access to middle-mile and long-haul providers specializing in quickly transmitting data across a geographical region. These carry data from outlying areas into major metropolitan areas where, if necessary, it can be sent around the globe. The Eastern US shares many undersea cable connections with Western Europe,Europe, asjust welllike asthe Western US connects to China and Japan.
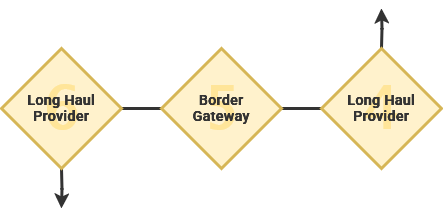
Through the Border Gateway Protocol, data can find a route across this patchwork of autonomous and independently-owned network systems. This process relies on the mutual agreement between ISPs that every network system will act as a neutral peer to all other networks ensuring that messages will always be passed along towards its destination. If these data packets contain any erroneous or fabricated metadata, they will likely get lost during this exchange process.
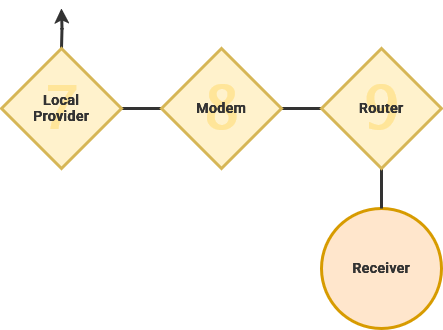
From here, packets will attempt the most direct route to it's destination while performing the same process in reverse. Data transits through regional and local internet infrastructures. Finally, the data enters the intended router and reaches its destination.
LocalConnected Communities
Computer networks consist of nodes – which are devices that are seeking to communicate – as well as the links between them. Under some circumstances, nodes will connected to other nearby nodes and creating a mesh that data can traverse along while seeking it's destination.

Occasionally, edge networks form around connectivity bottlenecks that arise in rural, disconnected areas. This can increase the cost of internet service, as well as effect the overall speed or availability of internet access. These often arise along geological boundaries – such as mountains – as well as within marginalized and disconnected communities.
What areas are disconnected? Why might that be?

Networks, like much of computing, rely on abstraction to allow people to comprehend the scale of infrastructure required to power telecommunications at this scale. In order to build a global infrastructure, digital technologies have created a stratified system that simplifies data shared in between these layers.
You don't need to understand electrical engineering to build a computer system from its constituent parts. Similarly, data isn't concerned about the path it takes – just that it has one. Data follows the path assigned to it and does not consider routing options itself.
Scale is a foundational way these systems are abstracted when trying to classify them. This is important to consider because differently sized networks have unique, specific needs. Your home network only needs to juggle a handful of people's data, while a college campus will be handling much more traffic.

Personal Area NetworksNetwork
WithinWhile your localphone areais network, all of your devices connectconnected to your localheadphones routerthrough BlueTooth, you are creating a Personal Area Network. These, as the name implies, operate on a smaller and more intimate scale. PANs utilize wired and wireless technologies connected to a central computing device – sometimes provided by your ISP. Within this local network, powered by your router, your devices are givenlike a unique numerical identifier known as an IP –cellphone or internet protocol – address.laptop. For
this
Local lookArea likeNetwork
A Local ThisArea numberNetwork allows us to designate over a network of multiple computers, which one we are specifically trying to speak to. There are three "reserved" IP address ranges for local networks: 10.0.0.0, 172.16.0.0, 192.168.0.0. Your local router – tasked with assigning IP addresses to everyone – acts as a gateway forcontains all of the nodes and links within a limited (often architectural or regional) area. This includes desktop, television and console devices attached by cable, as well as other devices connected wirelessly.
This could be as small as your home or some larger contained area – like a college campus or corporate headquarters. These institutions must subscribe to Internet service – just on youra larger scale. They may hundreds of interconnected wireless routers blanketing a mesh network over a large physical area.
Universities can have several campuses and corporations may have branch offices at different scales. A Virtual Private Network creates a private tunnel connecting two geographically separated LANs into one. This enables devices over vast distances to communicate as if they were nearby. This can be accomplished invisibly through hardwired infrastructure, as well as on a device-by-device basis by connecting to a VPN server with appropriate credentials.
Each Local Area Network has a modem responsible for transmitting data to and from an Internet Service Provider. This hardware is used to modulate – or translate – data into a signal that can be sent along a physical cable, radio wave or other connection.
The router connects to the Internet.
When connecting devices on a local network, a few types of networking devices can be used. The routerand orchestrates communication between all the devices connected to it,it. whileWhile hubsconnected, each device is assigned a Private IP Address – a unique identification number on that network. This allows devices to quickly and switchesintentionally canexchange createinformation smallerover subnetworks.your Thesenetwork, even if there is no access to the outside ofWorld Wide Web.
A LAN IP address could hypothetically be 192.168.68.100 or 10.0.0.100.
Modern routers often incorporate wireless connectivity through the Wi-Fi standard – which turns data in radio waves that can be puttransmitted togetherwirelessly to devices. Ethernet is a standard for enabling network device communication over a wire. Ethernet cables are given a category designation – with higher categories meeting the performance requirements of data centers.
Make flow in manya differentstraight configurationsline. Red icon pointing out unintended recipient.
When connecting computers to achievea thewired desirednetwork, efdectthere orare reacha specificfew requirements.devices that can incorporate physical cables to facilitate links between nodes. Judging solely by appearance, it can hard to tell them apart.
|
Router |
Hub |
Switch |
A repeater hub can connect many devices to the network,network on once, but itwill openly broadcasts all data it receives to every device connected to it. ThisThey can be cost cost-effective because theyof are based ontheir simple circuits,design, but they greatly increase the potential for snoopingdata andsniffing decrease– overallor performance.the data being intercepted by someone other than the intended recipient.

On
theAother switchhand, isa switching hub behaves more intelligentintelligently and willby only sendsending data to it's intended recipient. This requirerequires more powerful , and expensive, internal hardwareelectronics to process the information being transmitted through it.it, Thisbut ultimately results in higherbetter performancereliability and better regulated security.
Wide Area Network
IndividualThese LANs,disparate Local Area Networks – such as your network – as well ashome, your neighbors, city, county and state – are conglomerated together into a Wide Area Network or WAN.
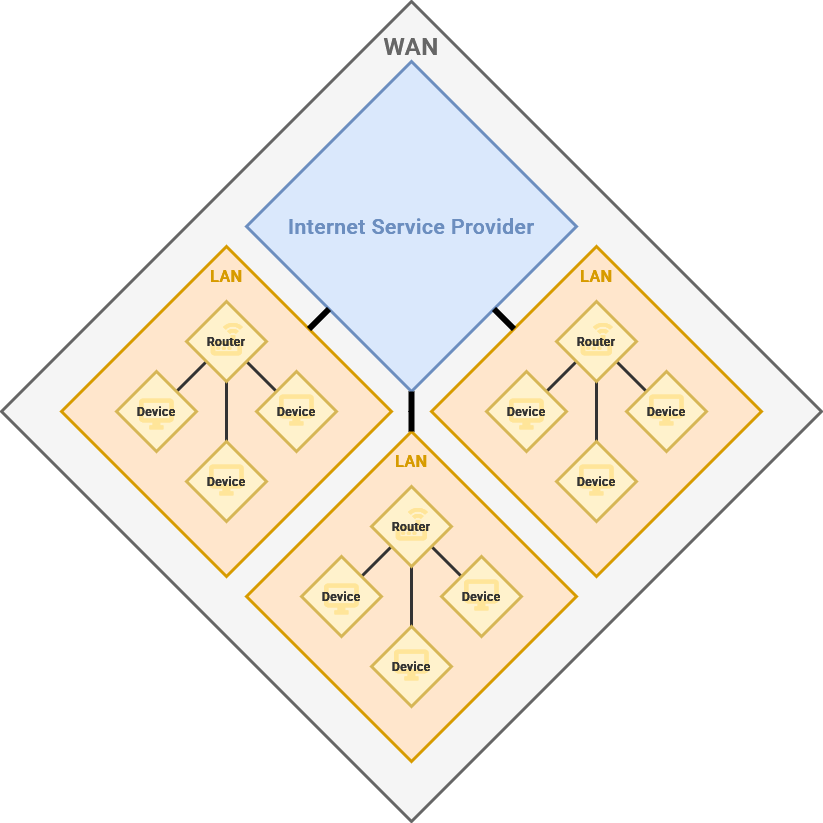
Your router,modem, acting as the gateway for your devices to the internet, is also assigned a Wide Area NetworkPublic IP Address.Address. Similar Forto example,a thephone IPnumber addressor forstreet example.comaddress, this is "92.122.244.34" allowing anyone in the world to know exactly how tonetworks locatefind theeach web serverother over the internet.

VPN connecting two lan over theworldwide internet to create a secure, private and enceyoted tunnel for all data between the two, allowing them to operating as one Lan. A computer can act either as a server - that broadcasts the service - or a client that connects to it.infrastructure.
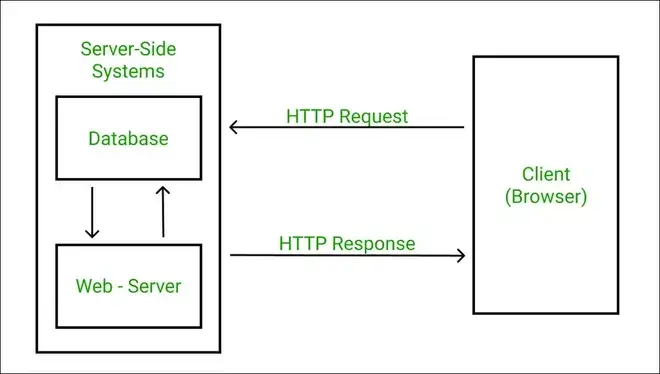
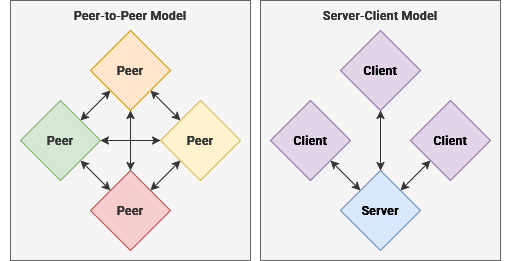
The modern internet, as we know it, predominately operates within the sever-client model. This means that one computer – a server – is used to respond to the requests of other computers – known as clients.
When visiting a web url, such as example.com, it is converted to an IP address of a server by the DNS. By connecting to this IP address through your web browser, you can access the website that is being served to clients. Peer-to-Peer networks, where each computer acts as both a server and a client, are becoming more popular for services like BitTorrent, OwnCloud and Social Media.
DNS
Domain names
For example, the IP address for example.com is "92.122.244.34" allowing anyone in the world to know exactly how to locate the web server over the internet.
Open Standards
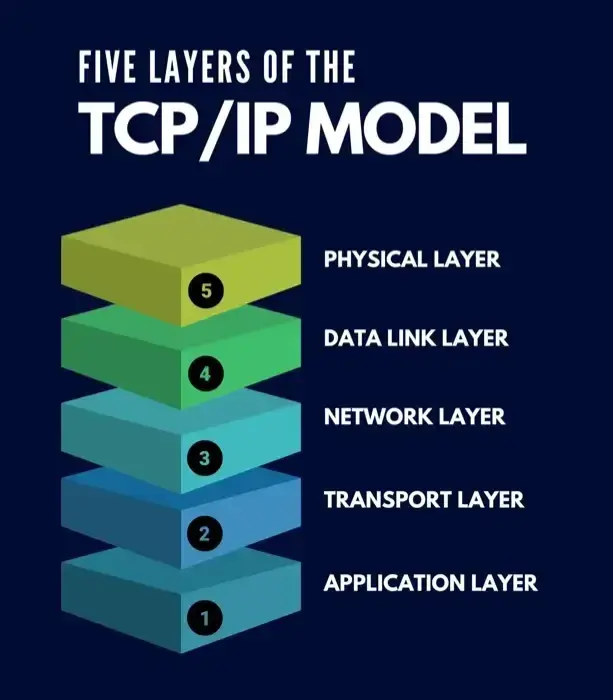
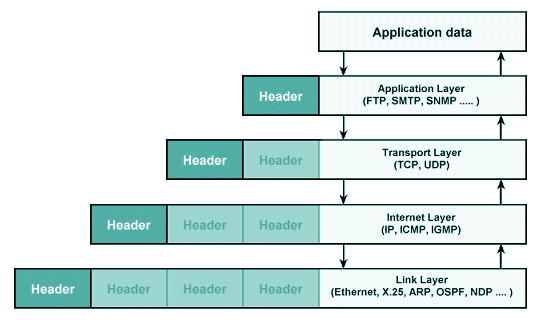
Data transmission over the internet is built upon a technology first explored in 1960s with ARPANET. By the 1980s, the standard for communication over the internet – known as TCP/IP or more commonly the Internet Protocol Suite – was first implemented. Simplified, access over the internet is broken into four alayers:
Each of these layers provide standards for how to ensure each layer can communicate with other devices through this protocol. At each level, we are ensuring that all nodes on the network are speaking a common language.
- Physical Layer: This layer handles how data signal is encoded and physically transmitted over wires. This layer can function in different ways, depending on your internet connection type – such as internet over coaxial cable or fiber optic cable.
- Link Layer: This layer handles how data is transmitted over the network through physical hardware such as Network Cards and Ethernet cables. This also includes hardware level identification of devices on the network, through a MAC Address, that allows the router to know which device is which, even when it hasn't been previously connected before.
- Network Layer: This layer dictates how nodes can find each other across the network, utilizing IP addresses and routing to determine how to get from point A to point B. This is the layer where devices are provided IP addresses on their local and wide area networks, and traces the optimal route between two nodes using these IP addresses. Data transmitted over this layer is broken up into small segments that are easier to transmit. TCP and UDP.
- Transport Layer: This layer is responsible for ensuring that individual nodes can communicate with each other reliably and without errors. Now that data is broken up into small segments for transmission, we can chose to transport this data in different ways.
- Application Layer: This is the top most layer of the internet where protocols such as HTTP and SMTP are implemented. This is the layer that most people interact with when they are browsing the internet through operating system applications. At this level, the user doesn't need to consider how or where the data is traveling. It happens almost invisibly.
In between each layer, as our data transmission is broken into smaller and smaller pieces by our physical device and the software installed on it, "metadata" is appended to each small packet. These "headers" detail how this packet of data relates to other packets, as well as the path taken and route still in progress.
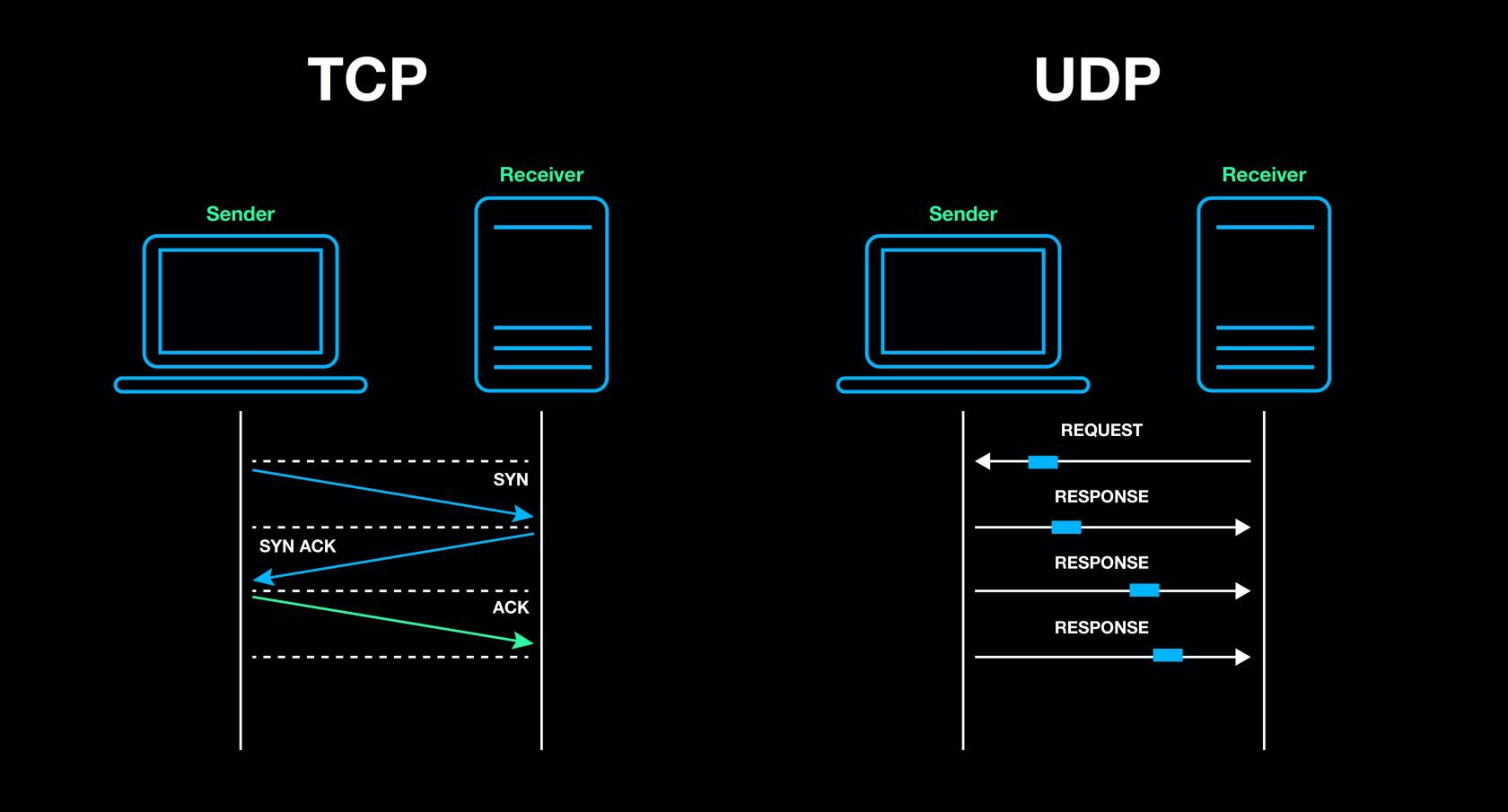
Once two nodes on a network have initiated communication - such as your laptop connecting to a remote server – through the internet later by up address, they need to confirm the method for communication. When developers design an application, they can choose to transmit data over the internet through two protocols, both with benefits and drawbacks.
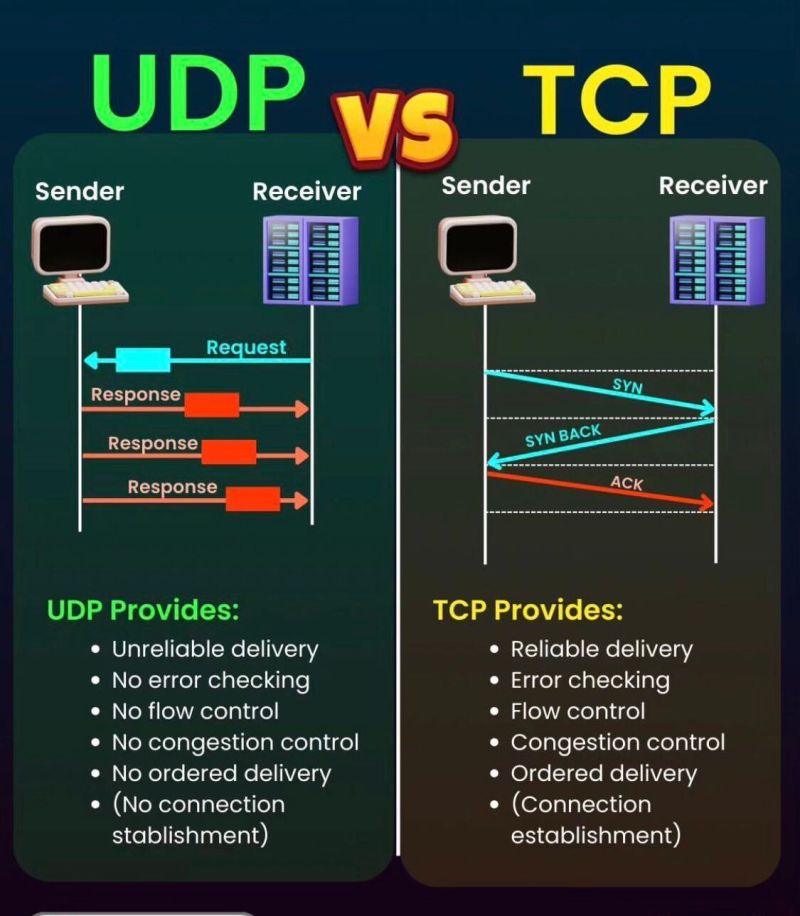
TCP ensures that all data will arrive with perfect fidelity and in the current order. In order to do this, both devices need to "handshake" – or agree to initiate a data connection between them. Packet 1 will be received before Packet 2, and so on. Each data packet is individually verified to ensure it was received correctly and, if it isn't, it is transmitted again and again until it is properly received. This is more process intensive and can take longer because it transmits one packet at a time. This protocol is used for HTTP, the backbone of the world wide web, and TLS, which encrypts web traffic and verifies the identities of all nodes.
UDP, on the other hand, allows a client to begin rapidly sending data to a server without first needing to "handshake". Packets can be transmitted in parallel, meaning that the server will not receive data in any particular order or within a specific time frame. Packet 2 could be received first, followed by 1 and 3. In the event that a packet is never received or fails basic integrity checks, the server is made aware of the error but the data is never transmitted again. This is more common for time-sensitive applications, online video games or live streaming services because it may be preferable to risk losing data then it is to receive it late.
Ports: software-based channels that allow multiple services to exist on one computer. They also allow them to communicate over a local network with great complexity and versatility, without needing a domain name. This allows services to communicate behind the scenes, away from the internet. These ports are also often reserved for specific protocols, such as HTTP, HTTPS, SSH and DNS.